In this section, we will look at Metasploit Community. This is a web GUI that uses Metasploit, but it has features other than exploiting vulnerabilities. It can be used to discover open ports, just like Zenmap, and install services, but it doesn't stop there. It also maps these ports and services to existing exploits in Metasploit and existing modules. From there you can literally exploit a vulnerability straight away using Metasploit. Let's see how we can use it, and it will become clearer what it can be used for.
The tool is not included in Kali Linux. We need to download it from https://www.rapid7.com/products/metasploit/metasploit-community-registration.jsp. We will also need to use our email address because we will need the product activation key, which they'll send to the email that we enter when we download. Once we download this, we're going to navigate to our Downloads using the cd command to change directory. If we do ls to list the current files, we will be able to see that we have the installer metasploit-latest-linux-x64-installer.run file downloaded. The first thing we need to do is to change the permissions to an executable so that we can execute this file. To change the permissions in Linux, you use the chmod command, and then we will put in the permissions that we want to set, which is executable, +x, and we are going to put the filename, which is metasploit-latest-linux-x64-installer.run. Now, we will launch the command, which is as follows:
chmod +x metasploit-latest-linux-x64-installer.run
And if we do ls we will see that there is text that will be highlighted in green, which means that it's an executable:

To run any executable in Linux all we have to do is type in ./ and enter the filename. The ./metasploit-latest-linux-x64-installer.run file will run this executable for us. Now, we will just run through the process.
The installation is very simple:
- First, we click on I accept the agreement, and then we click Forward. We then select where we want to install it:

- It will ask us whether we want to start Metasploit as a service every time the machine starts. We can pick Yes or No. I prefer to pick No, but you can set it to Yes. Then the Metasploit UI will start automatically every time your computer starts. Click on Forward:

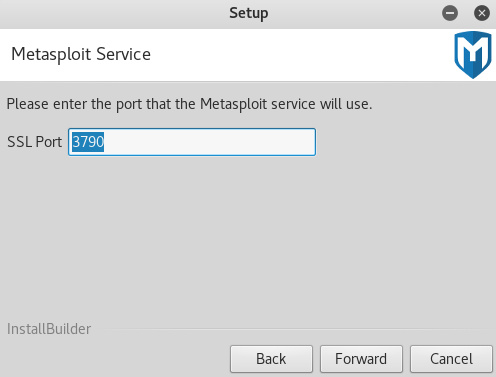
- Then it's going to ask us for the SSL Port that will be used. Because the service runs as a web GUI, we can set that to anything we want, but we are going to leave it as 3790:
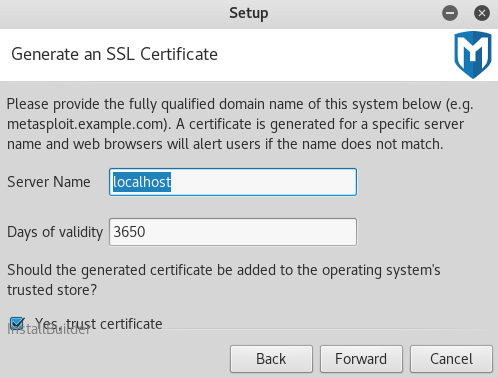
- And then it's asking us for the Server Name, and we are going to keep it as localhost because it's being installed on our localhost:
- Database Server port; again keep this the same, don't change it. Then there is the thin cluster port; again, keep this the same, 7337. These are all configurations for the program to run. We don't really need to mess with them. Only change them if you already installed the program and it won't let you have the same port, but usually it should keep them the same:

- Now, it's saying it's ready to install. Once you press Forward it will install it for you and it will ask you for a username and a password for the web interface. Set that as well, pick a username and a password, and the process will finish up smoothly.
Now, once we finish the installer we want to run the metasploit service. Because it's going to be installed as a service, as a web server, when we want to use Metasploit Community we will have to run it using the service command, the same way we run any service in Linux. We enter service metasploit start to start that service. Once the service has started, all we have to do is go to a browser and navigate to https. Make sure to put https not http://localhost/, and then we enter the port that Metasploit runs on, which is 3790. Press Enter. Now it's asking us to log in. We log in using the username and password that we picked while we installed the program, and then we will be able to use it. We'll be talking about logging in and using the tool in the next section.
