In this section, we are going to learn how to get information about the technologies used by the target website. We're going to use a website called Netcraft (https://www.netcraft.com), and we're going to put the target address, select our target as isecur1ty.org, and click on the arrow:
After, click on Site Report:
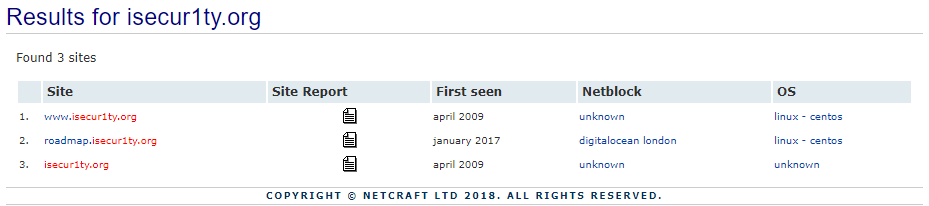
In the following screenshot, we can see some basic information, such as the Site title, a Description, Keywords, and when the website was created:

Scrolling down further, we can see the website itself, the Domain, the IP address, and just as we saw in the previous section, the Domain registrar, which is the company who registered the domain for isecur1ty:
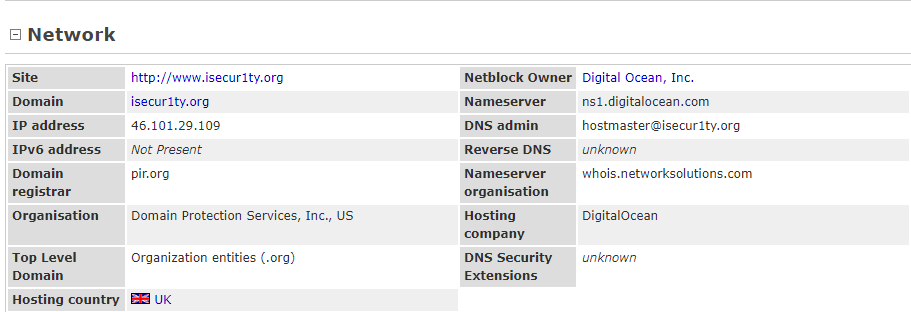
In the preceding screenshot, we would normally see information about the organization, but here, we can't , because isecur1ty is using privacy protection. Usually, we should be able to see such information and even more.
In the preceding screenshot we can see that it's hosted in the UK, we can see the Nameserver, which is ns1.digitalocean.com, and again, if we just go to ns1.digitalocean.com, we will discover that this is a website for web hosting.
Now, we know this is a web hosting company, and in worst-case scenarios we can use this or try to hack into ns1.digitalocean.com itself to gain access to isecur1ty.
Scrolling down further, we will see the Hosting History of the hosting companies that isecur1ty used, and we can see that the latest one is running on Linux with Apache, the same server that we saw in the previous section, 2.2.31 with Unix mod_ssl and all the other add-ons:

Again, this is very important to find vulnerabilities and exploits on our target computer:
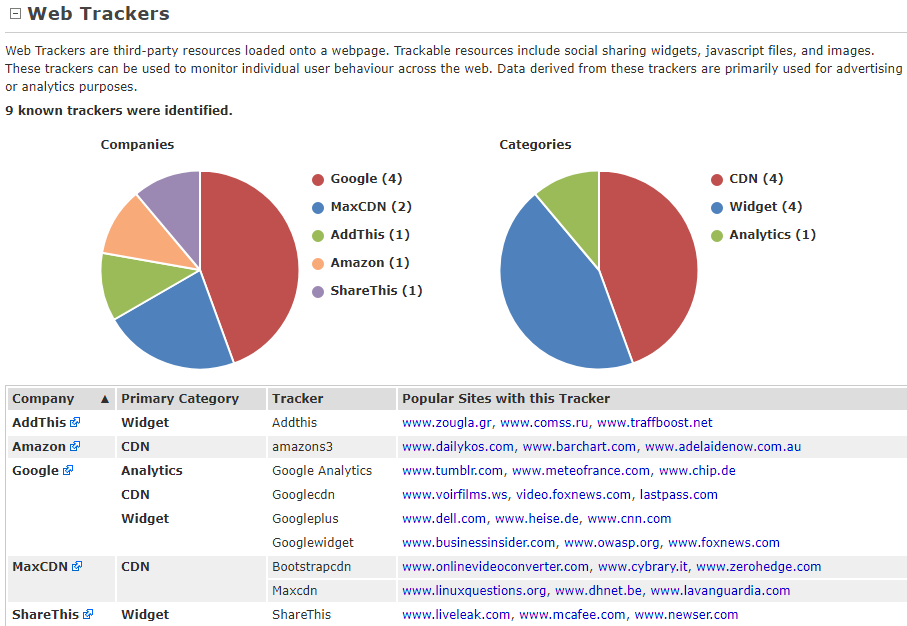
Scrolling down to Web Trackers, it will show us the third-party resources or applications used on our target, so we can see that our target uses Google, MaxCDN, and other Google services. This could also help us to find or gain access to the target computer:
The Technology tab is one of the most important tabs or sections in here, because it shows us the technologies used on the target website:

We can see in the preceding screenshot it's using the Apache web server, and on the Server-Side, we can see that the website uses PHP, which means the website can understand and run PHP code. This is very important because, in the future, if we manage to run any kind of code on our target, then we know the code should be sent as PHP code. To create payloads on Metasploit or on Veil-Evasion, we should create them in PHP format and the target website will be able to run them because it supports PHP. On the Client-Side, we can see in the preceding screenshot that the website supports JavaScript, so if we run JavaScript, or if we manage to run JavaScript code on the website, it won't be executed on the website; it will be executed on the users side who are viewing the website, because JavaScript is a client-side language and PHP is server-side. If we manage to run PHP code, it will be executed on the server itself. If we manage to run JavaScript, it will be executed on the users or the peoples machine who visit the website. It's the same with jQuery. This is just a framework for JavaScript.
Scrolling down, we can see in the following screenshot that the website uses WordPress Self-Hosted software. This is very important. Netcraft will also show any web applications being used on the website:
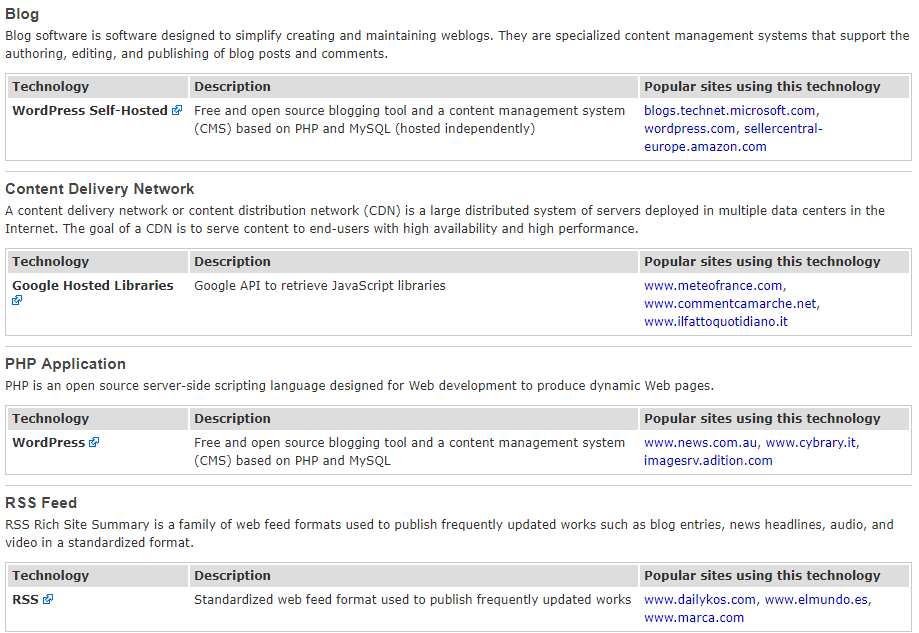
WordPress is just a web application, so we could see other examples in our case, and it's an open source web application, there are a lot of other websites might have. The good thing is we can go and find exploits or vulnerabilities within the web application. If we are lucky enough to find an existing one, then we can go ahead and exploit it on the target website. For example, we have WordPress in our example, so if we go to https://www.exploit-db.com/ and search for WordPress, we'll manage to find lot of exploits related to WordPress.
There are different versions of WordPress. We need to make sure that we have the same version as our target. We'll look at examples to see how to use exploits, but it just shows how powerful information gathering is. Scrolling further, we can also find other information, such as that the website uses HTML5 and CSS, and all that kind of stuff:
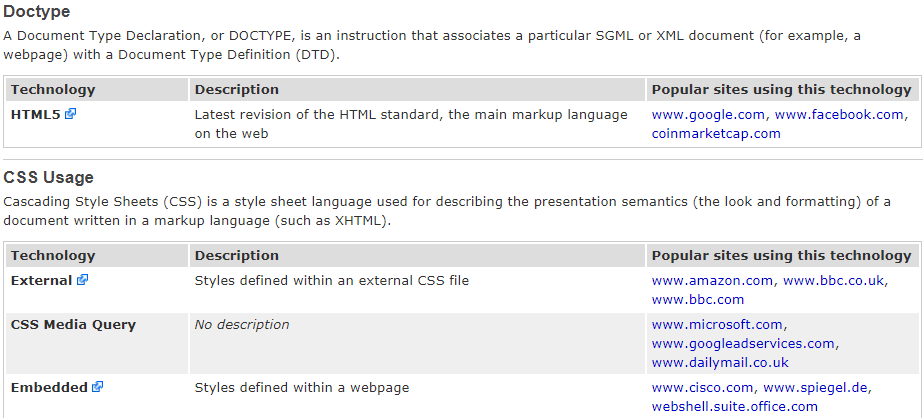
Hence, Netcraft is really useful for getting to know the website. We gathered information regarding the site—that it runs on PHP, and runs JavaScript. It uses WordPress, so we can use WordPress to hack into the website, and if we scroll up, we also discovered the web hosting of the website. Therefore, in worst-case scenarios, we can try to hack into a web hosting server and gain access to our target website.
