The Trojans we've created so far are amazing; they can bypass antivirus programs – they run two pieces of code, the first one runs in the background, which runs our own code and does what we want it to do, such as opening a port or connecting back to us and giving us a shell, and it runs another piece of code that the user expects. It could display an image, play an MP3, or display a PDF file. This functionality makes it very difficult to detect, so the best thing to do is to check the properties of the file and make sure that it is what it's claiming to be. In the following screenshot, we have a Packt image and we can see that it's a .jpg, so it looks like a picture, it has an icon, and if we run it we will get a picture, like we saw in Chapter 13, Client-Side Attacks - Social Engineering:

Right-click on it and go to Properties. When we go to Properties, we will see that this is an application, not a picture:
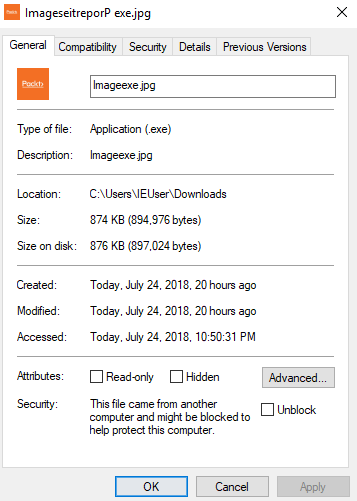
The same goes for PDFs and MP3s; it should say MP3 if it's an MP3, it should say PDF if it's a PDF, and it should say .jpg if it's a jpg. But in this case, it's telling us that it's an executable. Going through the Details, we will see that it is an application and not a picture – if it was a picture, it would tell us that it was a picture:

From this, we'll know that we're being tricked. We can also play with the filename and we will be able to reset it; if we rename the file to anything else, we will see that it's an .exe file and not a .jpg. If we change it to test, we will see that the name has been changed to test.exe:

Now, let's assume this Trojan was combined with an executable. If we run it, we expect to get .exe and an application. Let's assume that it's combined with Download Accelerator Plus software, instead of being combined with a picture. This task is going to be more difficult because we are expecting an application anyway. With the picture and with the PDF, Windows will tell us that we are trying to run an executable, but if we are expecting an executable, then we are going to run it anyway, such as with DAP. It will play the executable we are looking for and the executable will send a reverse session to Kali.
Go to a tool called Resource Monitor, and from that tool, go to the Network tab. There, we will be able to see all the open ports on our machine:

We can see that we have port 8080 and it's connecting to the 10.0.2.15 IP address. Obviously port 8080 is not very suspicious, even if it was on port 80, it wouldn't look suspicious, and also, it's coming from a process called browser.exe, which is not very suspicious either. The suspicious part is the remote address; it's accessing 10.0.2.15 and we don't know what that is. If it was a website, putting the IP in the browser should take us to a website or to a server of that website. In most cases, if this is a hacker computer, it will not take us to a website, and then we will know that this person is an attacker.
To verify the attack, we can use a tool called Reverse DNS Lookup. It gives us an IP and tells us which website this IP belongs to, or which domain this IP belongs to. Let's look at an example on Facebook. Let's say we saw a suspicious-looking IP in our Resource Manager. We are actually going to get a proper IP address for Facebook by pinging:

We have seen the 157.240.7.38 IP; there is a connection on port 80 going to this IP. Copy this IP and use Google to search for Reverse DNS, open the first site, paste the IP, and click Reverse Lookup. We can see the IP that we saw in our resources:
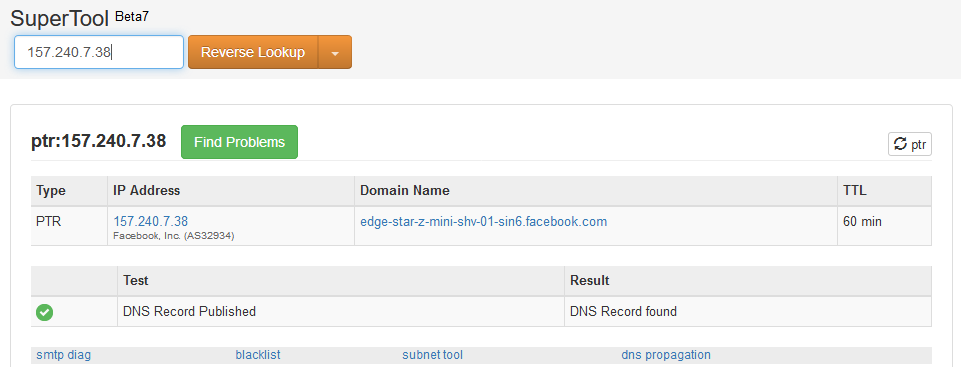
If it's for a proper website, then there is nothing to be concerned about; if it looks suspicious, then we will know that this is going to a suspicious person. Now, as we can see in the preceding screenshot, it's going to Facebook and we are browsing Facebook – this is normal, we are using Facebook so there's a connection between us and Facebook.
