After the scan is over and we can see our website on the left, clicking on it will show us some results from the Spider when it was looking for the files:

The very interesting part is the Alerts in the following screenshot. We can see all the vulnerabilities that have been discovered:
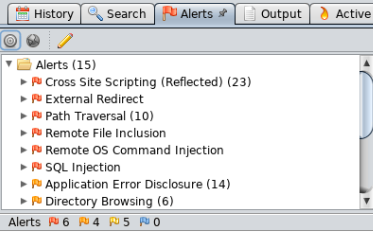
At the bottom-left of the preceding screenshot, we can see that we have 6 red flags, the High Priority Alerts, we have 4 orange flags, 5 yellow flags, and 0 blue. These are organized in order of severity.
Clicking on any of the categories will expand it and show the threats that have been found, for example, clicking on Path Traversal (10), we'll see all the URLs that can be exploited to read files from the server:

Clicking on any of the sites, we will see the HTTP request that was sent in order to discover this:

The following screenshot shows the response and why the tool thinks that this is vulnerable, and we can see that in the response the tool was able to get the contents of /etc/passwd:

In the following screenshot, we can see the URL, the tool used to exploit the vulnerability, and we can see a Description of what the current vulnerability is and how it has been exploited:

We can also see Risk, which is High. We can see Confidence—how confident the tool is about the existence of this vulnerability. We can also see that it's been injected into a page and the Attack is trying to get /etc/passwd. So, right-click on the page and click Open URL in Browser:

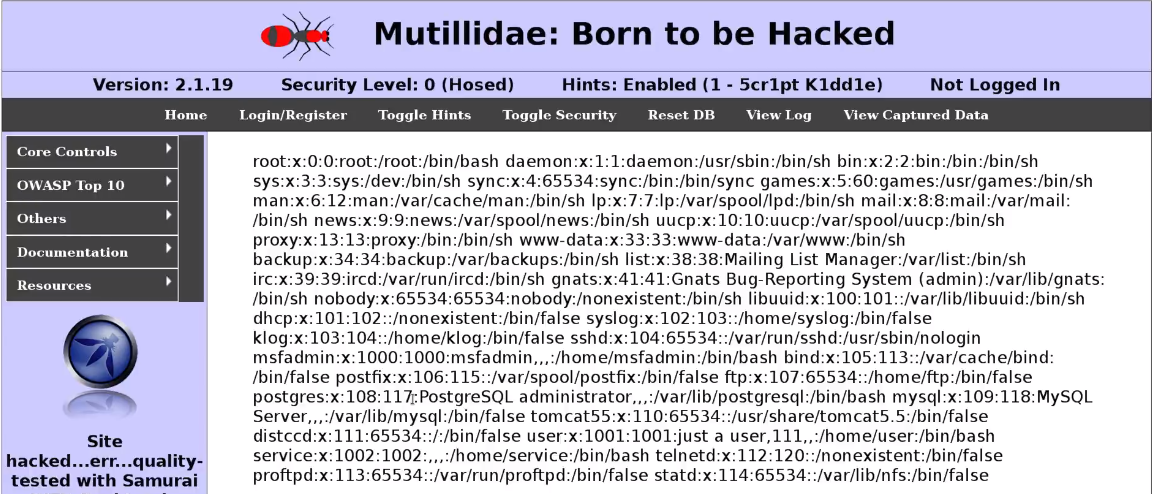
As we can see in the following screenshot, the tool has exploited the site for us. It shows us the output for the vulnerability, and we can read the contents of /etc/passwd:
Let's have a look at another example, for example Cross Site Scripting. Again, the tool also checks for POST and GET parameters. Sometimes, when the injection is sent in textboxes, or even sent without textboxes, if it's sent in a POST parameter, we won't see it in the URL, so it actually checks for POST and GET. You can see in the following screenshot, it found a vulnerability in the POST request in the register page, and it also found one in a GET request:

Again, right-clicking and opening in the browser will execute it for us, and we can see that the code has been executed:

Again, we can find the URL of the execution from the address bar in the browser. If we want to use it for any other tools, we can see it in tool as well, the URL that's being used to exploit the vulnerability.
Let's just have one more example of SQL Injection. Again, click on the link:
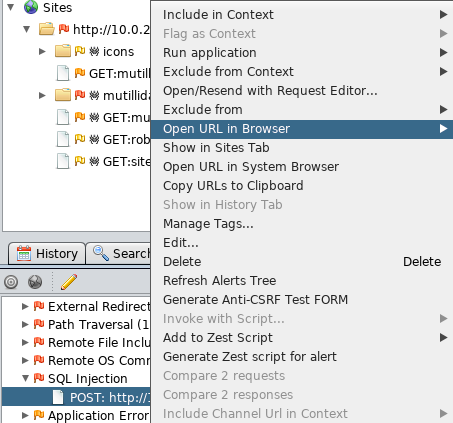
It will show us the URL and it will show us the Attack that it used, ZAP' AND '1'='1', which is in the Parameter password, and if you remember, we actually did exploit this parameter manually:

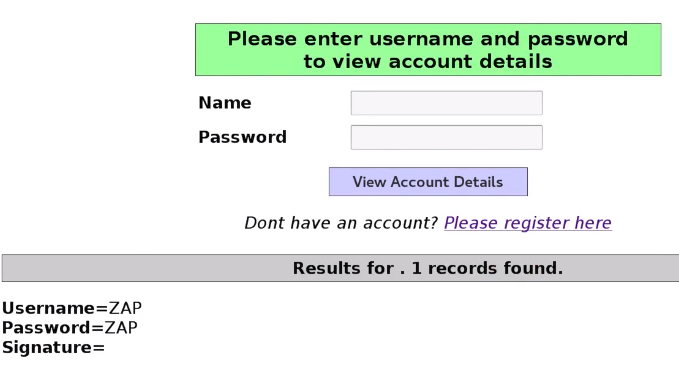
Opening the link in the browser will show us that the injection is working, and it's using a username and a password called ZAP:
So, the tool is very simple, very powerful, and very useful. We can play around with it, we can play around with the proxy and with the options, and see how we can enhance the results and achieve even better results.
