OK, now let's see what can we get using the email of the target person, which is [email protected]. In Maltego (and we are going to add a new entity of an email address), go to Personal | Email Address, drag and drop it into the graph, and set Email Address to [email protected] from Properties, as can be seen in the following screenshot:
We managed to get an email address from the target's blog. Using the email, we're now going to see what information we can get.
Right-click the entity as usual and we will see a list of Run Transform(s). For our example, click on To Domain [DNS] and click the Run button:

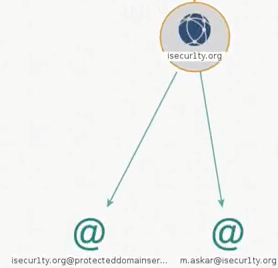
We can see that we got a domain name, which is isecur1ty.org. From the following website, we are going to try to get the email addresses associated with the website:

Right-click on the website, click on Email addresses from domain, and click on the Run All button to run all the transformers that will get the email addresses associated with the domain:

We have [email protected], which is the same person we found on the target's Twitter account:
Another thing that we can do from the domain is transfer to a website, right-click on the website, and click on To Website [Quick lookup]:
The following is the website:

From the website, we're going to look for email addresses associated with it, right-click on the website, click on Mirror: Email addresses found, and then click Run:

Once complete, we get two useless emails, so we are going to delete these two, leaving us with two good ones:
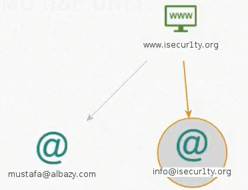
So we have [email protected], which is the same person that we found on Twitter, and we have [email protected]. Now again, we can just keep gathering more information about our target. We have enough information to start building up an attack strategy on the target person. In the next section, we'll discuss all the info that we gathered and we'll come up with ideas on how we can attack this person and hack into their system or into their accounts.
