The second machine that we will use is Metasploitable. Metasploitable is another Linux machine, and you can think of it as the opposite of Kali. Kali is designed so that you can use it to hack into other devices, while Metasploitable is designed so that you hack into it, so it's designed for people who want to learn penetration testing. It is designed so that it has a number of vulnerabilities, and we're going to try to use Kali Linux in order to hack into Metasploitable. Therefore, this is going to be one of the target, or victim, machines.
You can download Metasploitable at https://information.rapid7.com/metasploitable-download.html.
You will end up with a ZIP file, like the following. Once you decompress it, you will get a directory named metasploitable-linux-2.0.0.zip; double-click it, and you'll see the following files:
So, we're going to create a new machine, through the following steps:
- To get a virtual machine, we will click on New, and we will name it Metasploitable and change its type to a Linux machine. Then, hit Next, and give it only 1 GB of RAM.
- Then, we are going to use the existing virtual file option, unlike when we created Kali Linux (that is, when we created a new virtual hard disk). The reason for this is that the image we have now is actually designed for VMware Player. So, we're going to import the hard disk file, or the hard disk image, so that we have an installation ready without having to install it. We're just going to use an existing hard disk file. We will go into the Metasploitable directory and select the .vmdk file.
- Click on Open and Create. We are going to start the machine right now. This is what we will see when the machine is running and fully installed:
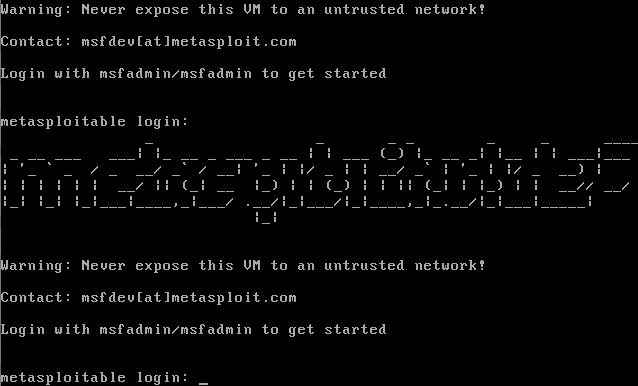
- We don't really need to install anything, as we just imported a pre-made installation, a ready hard disk. So, now it's asking for the username, msfadmin. The password is the same. We are now logged in:
This machine only has a Terminal, and it's giving you a warning that you should never expose this machine to an external internet connection because it is a vulnerable machine, designed to be vulnerable. It's only inside our lab, installed as a virtual machine, so nobody outside our lab can access it, which is a really good way of using it. As mentioned previously, in later chapters, we're going to discuss how we can try to hack into this machine. Again, don't be intimidated by the Terminal; we're going to be using it a lot, and we're going to learn how to use it step by step.
If we want to turn this machine off, all we have to do is type in sudo poweroff—just run the command. After asking for the admin password, the machine just turns off: