If we look at the backdoor, or the Trojan that we've generated so far, all it has is an icon that represents a file that the target person is interested in. When it's executed, it shows a normal file. And, at the same time, it's going to execute our code in the background, which will allow us to hack the target computer, or do whatever we want. The only problem with this file is that if we look at the end of the file, we can see that it has a .exe extension. In most cases, the target probably won't see the .exe extension because Windows is configured to hide it, but if it's not hiding it, then it's obvious that this file is an executable because it ends with a .exe extension. In this section, we are going to focus on how to spoof our Trojan and change it to something that corresponds to the file. If we're trying to make our backdoor look like a PDF, we can make it look like it has a .pdf extension; if we're trying to make the file look like an image, we want to make its extension look like a .jpg, a .png, or an extension that represents the image.
In our case, we're trying to make it look like an image, which means it should have a .jpg extension. To do that, we're going to use a right-to-left override character. We are just going to copy and paste it into our text editor so that when we are modifying things, it's clear to us what we are doing:
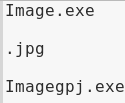
In the preceding screenshot, we can see the new filename that we want to use, which is Image, and this is going to have a .exe extension. Now, instead of .exe, we actually want to have .jpg, but that's not possible because if we do that, the file is not going to be an executable. To change the extension, we are going to try to get the text to be read from right to left, using a right-to-left override character. Because the text is going to be read from right to left, we're going to type gpj after the Image filename, but we're going to spell it from right to left. Again, this is just the extension that we want to use, but we're spelling it from right to left, so we're spelling it gpj instead of jpg.
Now, we want to put in a right-to-left character. When we put that character in the text, anything that comes in after that character will be read from right to left, so all this is going to be flipped and the Imagegpj.exe filename is going to be called Imageexe, and gpj is going to be read from right to left, so it's going to be .jpg. Let's perform it and we'll see what we mean by reading from right to left. To get that character, we're going to search for Characters in Kali and open the program:

Click on the Search icon and search for the right-to-left override:

If we click on it, we will see a button that will allow us to copy that character:

Click on Copy Character and that will copy the character for this example. Now, go back to editor and paste the copied character in front of gpj.exe:
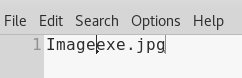
As seen in the preceding screenshot, if we paste it, everything is being read from right to left and the filename is going to be called Imageexe.jpg. If we are using this as a book or as something else, we want to think of a name that ends with "ex". Anything that ends with "ex" will be a good name to use. So, we have our name now and we are just going to copy the new name from the text editor, and then we are going to rename the backdoor file and we will have a file called Imageexe.jpg, as shown in the following screenshot:
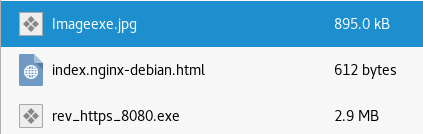
Now, we can send the new file to the target, but we don't want to send it like this because some recent browsers are removing the right-to-left override when downloading the file, so what we are going to do is compress the file to Imagejpg.zip:

This way, when the file is downloaded by the browser, it will not replace the right-to-left override. Copy the content, paste it into the evil-files folder, and then we're going to download it from the Windows machine.
Now, we will listen for incoming connections (we have already done this, so if a refresher is needed, go back to Chapter 10, Gaining Access to Computer Devices). Go to the Windows machine and download the file, which is located at http://10.0.2.15/Imagejpg.zip:
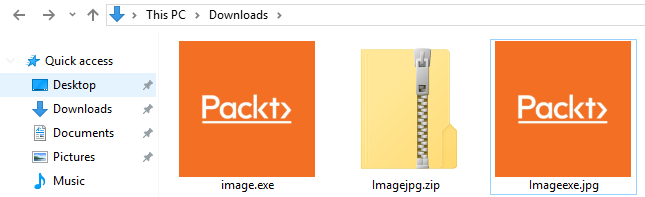
Uncompress the downloaded file and, as we can see in the following screenshot, the file has a .jpg extension. It has an image icon and, if we double-click it, it will actually show us an image, but, at the same time, it's going to execute our backdoor in the background:
So, if we go to the Kali machine, we will get a session from that computer, and, just to confirm this, we are going to run sysinfo. As we can see in the following screenshot, we are now inside that computer and we have full control over it:

We managed to do this using a file that looks and functions exactly like an image. This method can be used to make the file look like any other file type, so we don't have to make it look like an image; we can use this method to make it look like a PDF, a song, a video, or anything that we want. We can use the download-and-execute payload to combine the backdoor with any file, and then use this method to change the file extension to any file extension we want.
