The Basic settings section provides administrators with quick access to the Password Recovery flow, as well as links for setting up Two-step verification and user's access to Less secure apps.
Enabling the Two-step verification (2SV) login flow will require the user to provide a key coming from a registered device in addition to their username and password. Each generated key is only usable once, so without the device, the credentials are not enough to access the account.
You can choose any of the following options for two-step authentication:
- Security Keys that are provided by special devices, usually USB drives that one physically inserts in the machine, or sometimes it's a card that you tap to a Near Field Communication (NFC) or Bluetooth Low Energy (BLE) device. This is the safest option, but also more expensive to implement.
- A Google Prompt that shows on the user's Android or Apple device to confirm a login attempt. This is a very effective and easy-to-use way of doing this.
- Using the Google Authenticator app. This is a special application that generates single-use 2SV keys. This is basically a software version of a security key generator, so there is no need to buy specialized hardware. This is a very safe and cost-effective option.
The Two-step verification settings looks as follows:
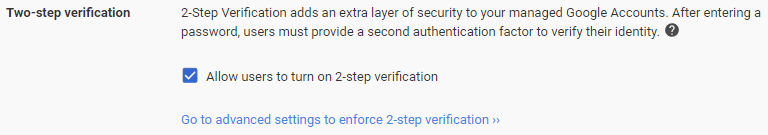
To implement Two-step verification, follow these steps:
- Enable Allow users to turn on 2-step verification.
- Click SAVE to apply changes. Optionally, you can define more details by following these steps:
- Click Go to advanced settings to enforce 2-step verification
- If you are handling more than one organization, you can select the one that you wish to set up these rules by selecting the name on the left menu:

-
- To set up a Group Filter to grant this privilege to only a specific part of the organization, follow these steps:
- Click SELECT on the bottom left menu:
- To set up a Group Filter to grant this privilege to only a specific part of the organization, follow these steps:
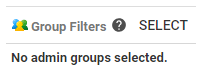
-
-
- Click on the group you wish to enable direct access to password recovery:
-
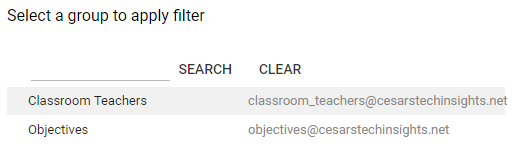
-
-
- Click DONE to apply the filter. You can see the targeted users at the top of the setup options:
-
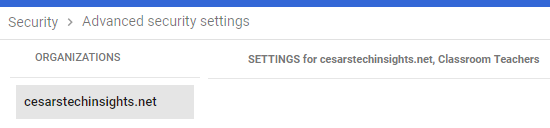
-
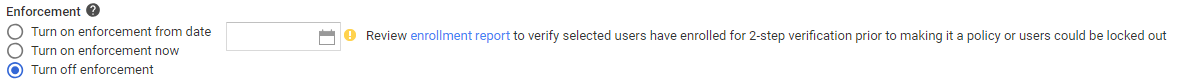
- Define the 2-step verification Enforcement policy for this group by selecting one of these options:
-
-
- Apply the enforcement after a certain date by selecting it on Turn on enforcement from date:
- Click enrollment report to see a report of this policy compliance by the users
- Turn on enforcement now will apply two-step verification immediately
- Turn off enforcement so users are never required to use it
- Apply the enforcement after a certain date by selecting it on Turn on enforcement from date:
-
-
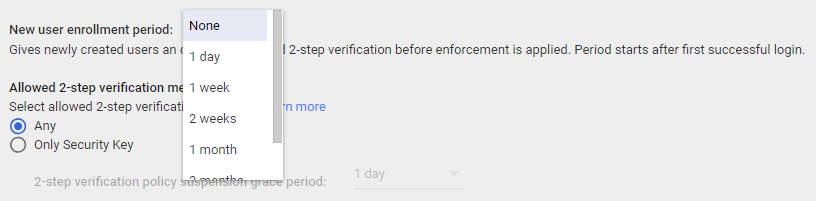
- Select how much time new accounts can go after activation before being required to use two-step verification on the New user enrollment period drop-down menu:
-
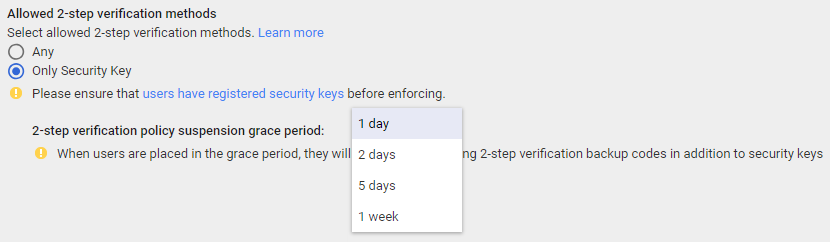
- Select the Allowed 2-step verification method:
- Choose Any to allow users to use a physical key and all web security flows
- Choose Only Security Key to require users to use a special physical security device to access:
- Select the Allowed 2-step verification method:
-
-
-
- Select a 2-step verification policy suspension grace period, which is a period that administrators give to users to be able to access using other security flows, usually while they are given a new key
-
-
-
- Select the 2-step verification frequencyto define if users can log in only once on selected devices, or whether they should always follow the 2SV
- At the Password recovery section, you can Enable non-admin user password recoveryto allow users that are not administrators to perform Password recovery so that they can regain access to their accounts without the help of an administrator:

-
- Click SAVE on the bottom left corner to persist changes
As an administrator, you can define whether the users within the domain can install additional apps, even if they are using a less secure sign-in technology, although this is not recommended. You can do this by following these steps:
- Click Go to settings for less secure apps, as follows:

Select the restriction level for Less secure apps. The options are outlined as follows:
-
- Disable access to less secure apps for all users is the recommended option and will completely prevent less secure apps to be used in the domain.
- Allow users to manage their access to less secure apps will allow administrators to allow specific apps. Use this only if you really need to use a specific app.
- Enforce access to less secure apps for all users will allow the free use of less secure applications, although this is not recommended.
- Click SAVE on the bottom right corner to apply your changes.
By setting up the basic settings, you have quickly covered the most crucial configurations, but there is still much more to cover; continue to the next section to learn how to set up Password management.
