Another awesome OSINT tool is OSRFramework. This toolset performs lookups using usernames, DNS records, deep web searches, and much more.
To begin, we can execute the osrf command on the Terminal to provide a description of the usage of the tool itself. Let's imagine that we need to obtain a list of corporate email addresses of our target company on a social media platform. The following are the components of OSRFramework that we can utilize in order to gather information from various sources:
- domainfy: Checks whether domain names that use words and nicknames are available
- entify: Extracts entities using regular expressions from provided URIs
- mailfy: Gets information about email accounts
- checkfy: Verifies whether a given email address matches a pattern
- phonefy: Looks for information linked to spam practices by a phone number
- searchfy: Performs queries on several platforms
- usufy: Looks for registered accounts with given nicknames
In our first example, we can attempt to obtain information about our target domain using the whois database. Using the domainfy.py --whois –n <target> syntax, the framework will begin querying whois and provide the results in a table format after a few minutes. In our example, I have used the domainfy.py --whois –n checkpoint command to specifically retrieve information for any domain that contains the name checkpoint.
The following are the results:

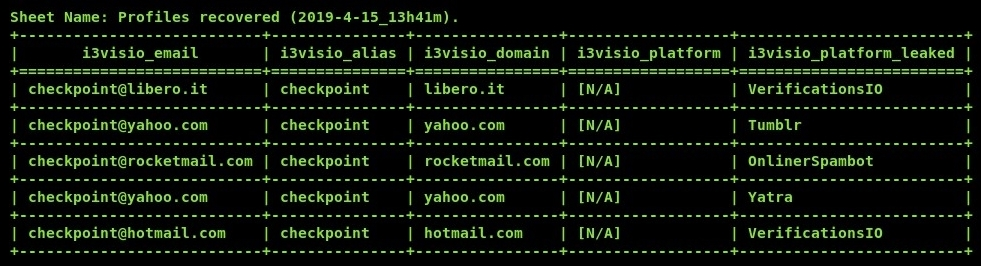
Next, we can attempt to obtain the email addresses of a given search string. In this second example, we are attempting to discover email addresses that contain the checkpoint string, which has been used on various websites on the internet. We can begin by using the mailfy.py –n checkpoint command. We will be presented with a table displaying the email addresses that fit our search criteria, domain, and platform location, as shown in the following screenshot:
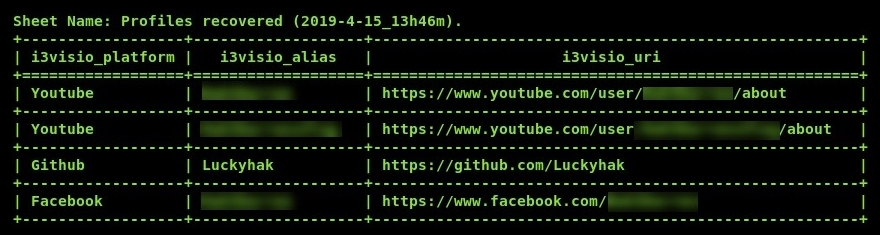
In our third example, we are going to use a string to search across all the services of OSRFramework. To achieve this task, use the seachfy.py –q string command on your Terminal. Once completed, the results are displayed and tell you about the location that was found, any aliases, and the URLs, as shown in the following screenshot:
Additionally, checking for telephone number leakage is simple with OSRFramework. Using the phonefy.py –n number command, OSRFramework will begin its search. The following screenshot displays the URL location and platform for a given telephone number:

In our final example, we can search for usernames. Using the usufy.py –n string command will allow OSRFramework to search for various online resources. In this example, I have searched for p@55w0rd1 as the username, and the following are the results:

As you have seen, OSRFramework is another very powerful tool within the Kali Linux platform. Using a tool such as this can save you a lot of time during your information-gathering process.
Having completed this section, you now have the skills to use multiple OSINT tools to gather specific and detailed information about a target organization. In the following section, we will discuss the topic of data leaks in cloud resources.
