In a null session, an attacker is able to log in to a target using a null account. A null account is an account that does not actually exist. How is this possible? Some systems are vulnerable to allowing anonymous login. Once a user is able to log in anonymously, the null user is able to retrieve sensitive information stored on the target.
We can attempt a null session enumeration from our Kali Linux machine (attacker) on to the target, Metasploitable, by using the rpcclient -U "" 10.10.10.100 command, as shown in the following screenshot:
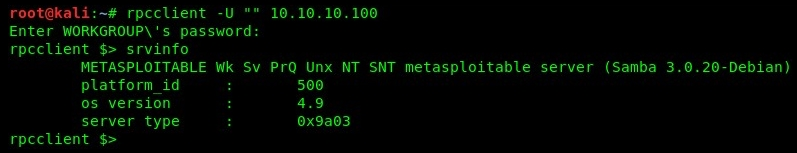
Using the srvinfo command, the target will return its operating system type to us. For a full listing of query commands, you can use the rpcclient --help command. Additionally, you can visit https://www.samba.org/samba/docs/current/man-html/rpcclient.1.html.
Keep in mind that not all machines are vulnerable to this type of attack, but it's still worth performing during a penetration test. In the next section, we will discuss user enumeration through noisy authentication controls.
