Metasploit is an exploitation development framework created by Rapid7 (www.rapid7.com). Metasploit contains many features and functions for penetration testing. There are many modules, such as exploits, payloads, encoders, and auxiliary. The auxiliary module contains port scanners, network sniffers, fuzzers, and a lot more to facilitate the information-gathering phase of a penetration test:
- To access the Metasploit interface, open a new Terminal and execute the following commands:
service postgresql start
msfconsole
- Once the user interface loads, the show auxiliary command will provide a list of all of the auxiliary modules within Metasploit. Let's use a simple example to demonstrate how to use a module: let's imagine you would like to perform a stealth (SYN) scan on a target. You can begin by selecting a module.
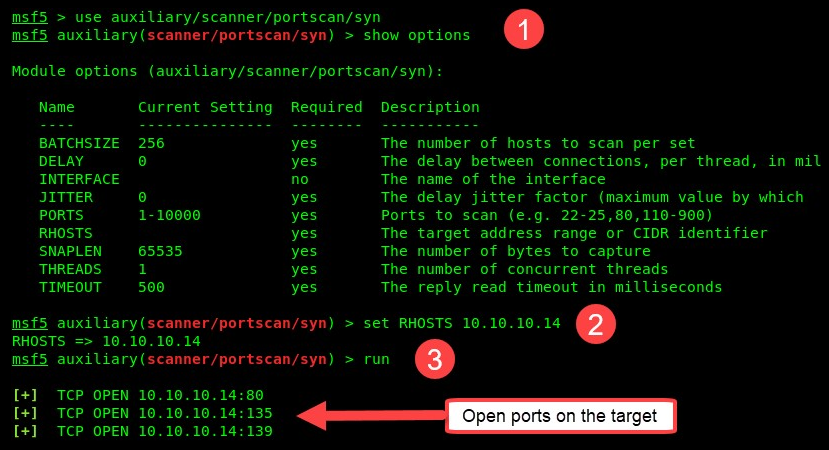
- Use the use auxiliary/scanner/portscan/syn command.
- Check the description and requirements by using the show options command.
- This module requires that a remote host is configured; use the set RHOSTS target command.
- To execute the module, use the run command.
- The following screenshot is a demonstration of a stealth scan on our Windows Server machine (10.10.10.14) and the results provided at the bottom indicate that various ports were found open:
- Additionally, to search for a module within Metasploit, using the search keyword syntax can be very useful as there are a lot of different modules in the framework, and learning them all can be very challenging and overwhelming.
In the later chapters in this book, we will dive deeper into using Metasploit to perform exploitation on target devices in our lab.
