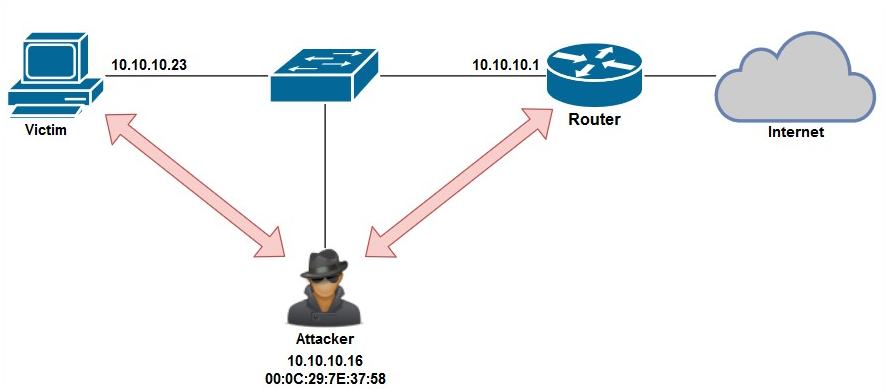
As a cybersecurity professional, you may be asked to help an organization identify any ARP poisoning attacks on their network infrastructure.
To explain the detection process of ARP poisoning, we'll use the following topology:
Using Wireshark, we can look for specific patterns of traffic between endpoint devices on the network. Using the arp filter on Wireshark, we will only be able to view ARP messages, as shown in the following screenshot:
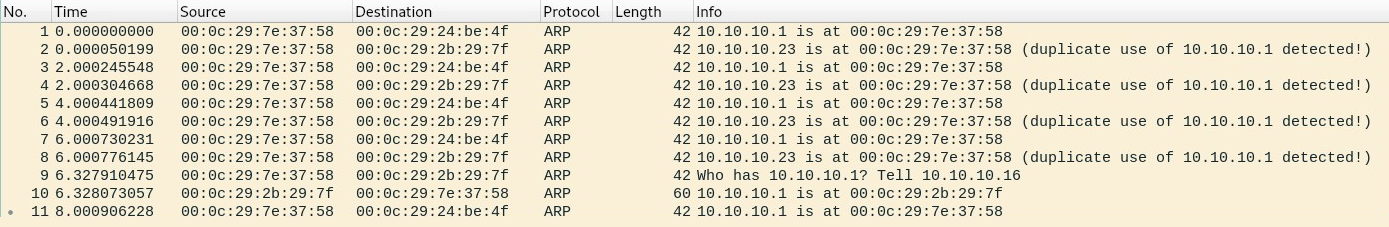
Within the Info column, a few of the packets have unusual descriptions. By expanding the information of Frame 1 within the Packet Details pane, we will be able to see that a sender (attacker) is sending a gratuitous ARP message (ARP reply) to 10.10.10.23 (a PC):
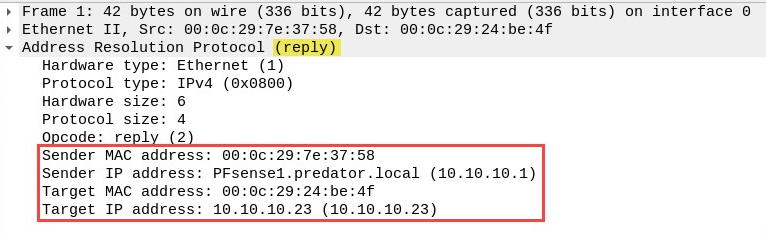
Frame 1 is telling 10.10.10.23 that the MAC address of 10.10.10.1 (the gateway) is 00:0c:29:7e:37:58. This will cause the victim to update its ARP cache to map 10.10.10.1 to 00:0c:29:7e:37:58. However, this MAC address belongs to the Kali Linux (attacker) machine.
The following screenshot shows the content of the frame that was sent from the attacker to the gateway (10.10.10.1), stating that the MAC address of the PC (10.10.10.23) is now 00:0c:29:7e:37:58:
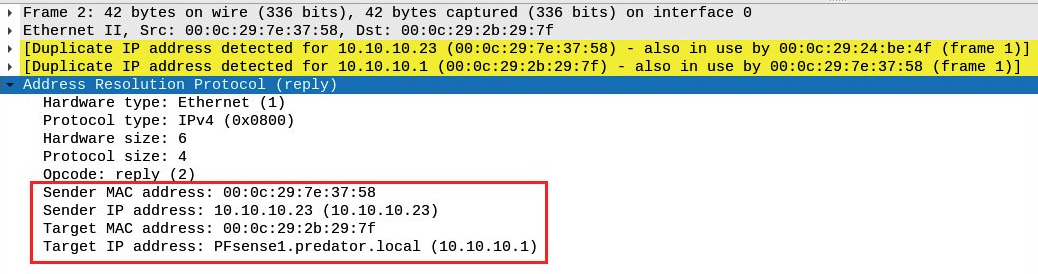
Additionally, Wireshark has been detecting the duplication of MAC addresses within the ARP frames and has issued a warning in yellow. Please keep in mind that Wireshark is a network protocol analyzer and not a threat monitoring application, and so human intervention is required to perform further analysis of network traffic. Security appliances and tools such as Cisco Stealthwatch, AlienVault SIEM, and OpenSOC can assist cybersecurity professionals in quickly identifying threats.
In this section, you have learned how to detect an ARP poisoning attack using Wireshark. In the next section, we will take a look at detecting suspicious activity on a network.
