Hping3 is a command-line tool that allows a user to analyze TCP/IP messages on a network. Additionally, Hping3 allows use to assemble network packets, which can be beneficial to a penetration tester in performing device and service discovery and offensive actions, such as a Denial-of-Service (DoS) attack.
Hping3 is a tool that can perform the following tasks:
- Host discovery on a network
- Fingerprinting host devices to determine services
- Sniffing network traffic
- Flooding packets (DoS)
- File transfer
As mentioned in the previous section, there are many servers and devices that have ICMP responses disabled as a security precaution. We can use Hping3 to probe a port on a target system to force an ICMP response back to our attacker machine.
To get started using Hping3, let's use the following steps to perform a port scan on port 80:
- We use the ping utility to send four ICMP echo request messages to our Windows Server machine (firewall enabled and ICMP disabled):
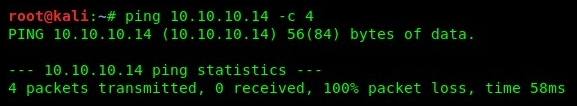
- Our attacker machine (Kali Linux) did not receive any responses from the target. A novice hacker would assume the target is offline and would probably move on. However, using Hping3 to probe a specific port by sending SYN packets will force the target to reveal itself. Using the hping3 -S target ip addr -p port -c 2 syntax, we get the following responses:
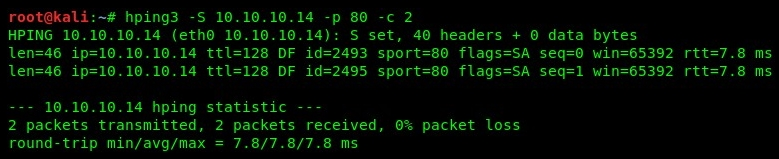
By looking at our results, we can see we have received successful responses from our target. This means that the 10.10.10.14 device is online and that port 80 is open.
- Additionally, we can take this step a bit further by performing port scanning on a range of network ports on a target device. Using the hping3 -8 20-1000 -S 10.10.10.14 command, we are able to perform an SYN scan on a range of ports from 20-1000 on our target. The following snippet indicates that ports 80, 135, 139, 445, 902, and 912 are open on our target:
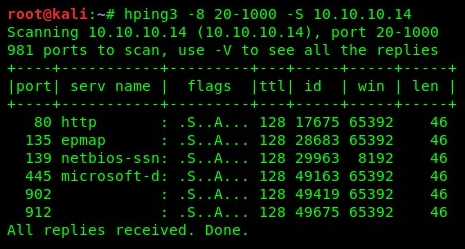
There are many more operators that can be combined when using Hping3; please be sure to check out the Help menu using the hping3 -h command on the Terminal.
Now that you are familiar with using Hping3 as a scanner, let's take a deep dive into performing enumeration on a target device.
