In a reflected XSS attack, data is inserted and then reflected back onto the web page. In this exercise, we will walk through the process of discovering a reflected XSS vulnerability on a target server.
To complete this task, perform the following instructions:
- Navigate to the bWAPP application and log in.
- Choose Cross-Site Scripting - Reflected (GET) and click on Hack to enable this vulnerability page:
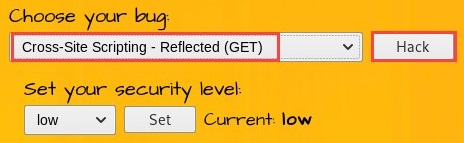
- Without entering any details in the form, click Go. Looking at the URL in the address bar of the web browser, you can see that the URL can be edited:
![]()
- To test whether the field is vulnerable to reflected XSS, we can insert custom JavaScript into the First name field. Insert the following JavaScript:
<script>alert("Testing Reflected XSS")
In the Last name field, use the following command to close the script:
</script>
The following screenshot shows what you need to do:

- Click on Go to execute the script on the server. The following pop-up window will appear:
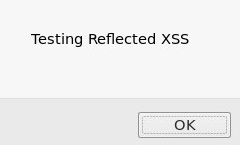
This indicates that the script ran without any issues on the target server; therefore, the server is vulnerable to XSS attacks.
In the next section, we will look at stored XSS.
