Over the past few years, cloud computing has become one of the fastest-growing trends in the IT industry. Cloud computing allows companies to migrate and utilize computing resources within a cloud provider's data center. Cloud computing providers have a pay-as-you-go model, which means that you only pay for the resources you use. Some cloud providers allow pay-per-minute schemes, while others use a pay-per-hour structure.
There are three big cloud providers:
- Amazon Web Services (AWS): Amazon's cloud service
- Microsoft Azure: Microsoft's cloud service
- Google Cloud Platform (GCP): Google's cloud service
A service that cloud providers usually offer to customers is a storage facility. The AWS storage facility is known as Simple Storage Service (S3). Whenever a customer enables the S3 service, a bucket is created. A bucket is a storage unit within the AWS platform where the customer can add or remove files. In Microsoft Azure, the file storage facility is known as Azure Files. Additionally, on GCP, the storage facility is known as Google Cloud Storage.
In the field of information security, we must remember that when a company is using a cloud platform, the data on the cloud platform must be secured, just like it should be when stored on premises (that is, when stored locally). Sometimes, administrators forget to enable security configurations or lack knowledge regarding the security of a cloud solution. This could lead to, say, an attacker discovering a target organization's AWS S3 buckets. Let's look at a simple example of doing that now.
In our exercise, we are going to use the S3Scanner tool. Follow these steps to get started:
- This tool is not pre-installed in Kali Linux, so we will need to create a clone of the GitHub repository by using the following command:
git clone https://github.com/sa7mon/S3Scanner.git
- Next, change directories to the S3Scanner folder using the cd S3Scanner command.
- Now, you'll need to install additional dependencies for this tool. Don't worry—the developers made this step very easy for us. To complete this step, use the pip install -r requirements.txt command.
- Once completed, we can now use our tool on a target's domain. Using the python ./s3scanner.py domain syntax, the tool scanner will create a domain for an AWS S3 bucket and determine whether it's accessible.
- The following screenshot shows the use of S3Scanner to check for any AWS S3 buckets on the flaws.cloud domain:
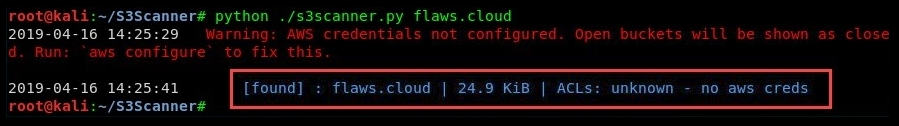
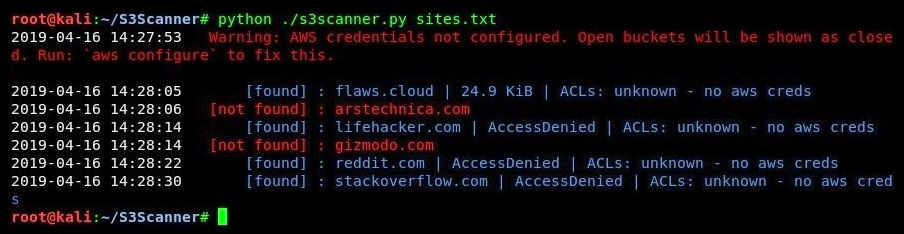
- One bucket has been found on the domain. Additionally, you can create a list of domains in a text file and query the entire file at once. The following is an example of querying multiple domains that are stored in the sites.text file:
- Furthermore, we can use the host command to resolve the IP address of the domain. Then, by using the nslookup utility with the ptr parameter, a reverse lookup can be performed, which will result in us getting the actual name of the AWS S3 bucket, as shown in the following screenshot:

Data leaks can happen on any platform and to any organization. As an upcoming penetration tester and cybersecurity professional, you must have knowledge of how to find them before an actual hacker does and exploits them. Companies can store sensitive data on cloud platforms, or even leave other data completely unprotected on a cloud service provider network. This can lead to the successful retrieval of data and accounts.
