An MITM attack is simply when the attacker sits between the victim and the rest of their network, intercepting and capturing network packets. The following is an illustration displaying an attacker (192.168.1.5) who is connected to the same segment as the victim (192.168.1.10):
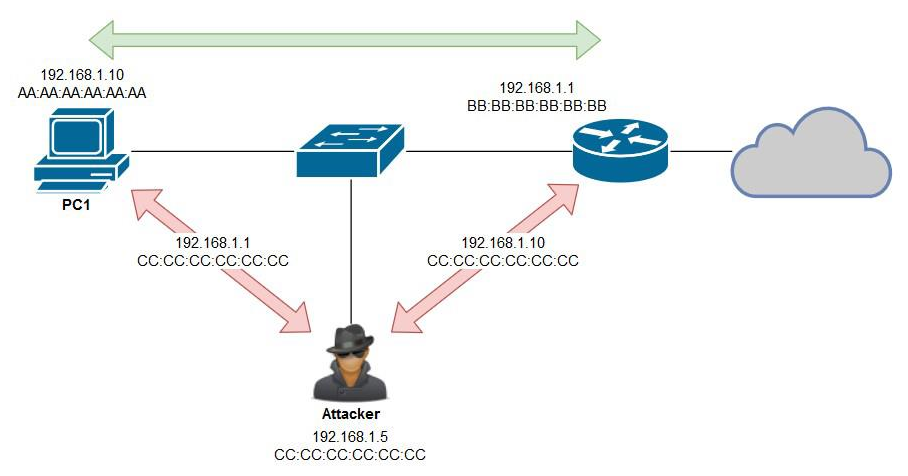
By default, the attacker machine will not be able to intercept and capture any traffic between PC1 and the default gateway (192.168.1.1). However, an attacker can perform ARP poisoning between the victim and the gateway. ARP poisoning is when an attacker sends a gratuitous ARP response to a device telling it to update its IP-to-MAC mapping. The attacker machine will send gratuitous ARP messages to the victim, telling the victim's machine that the gateway has changed to 192.168.1.1 - CC:CC:CC:CC:CC:CC, and to the gateway, telling it that PC1 has changed to 192.168.1.10 - CC:CC:CC:CC:CC:CC.
This would have the effect of all packets exchanged between PC1 and the router being passed through the attacker machine, which sniffs those packets for sensitive information, such as routing updates, running services, user credentials, and browsing history.
In the following section, we'll take a look at various tools and techniques for performing a successful MITM attack on an internal network.
