Within a corporate network, system administrators usually allow employees to access the internet through a proxy server. The proxy server usually improves performance and security, and monitors web traffic entering and leaving the corporate network. WPAD is a technique that is used on client machines to discover the URL of a configuration file via DHCP discovery methods. Once a client machine discovers a file, it is downloaded on the client machine and executed. The script will determine the proxy for the client.
In this exercise, we are going to use Responder on Kali Linux to capture a victim's user credentials. Before we begin, the following topology will be used in this exercise:
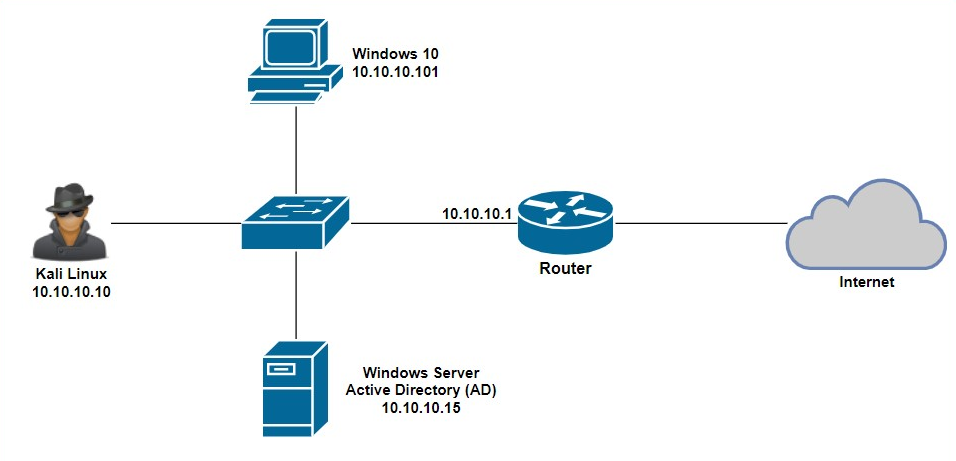
Using the following steps, we will be able to easily exploit WPAD in a Windows environment:
- Ensure that the Windows 10 client machine has joined the domain hosted by Windows Server.
- On your Kali Linux machine, change your working directory to the Responder location using the cd /usr/share/responder command.
- Execute the python Responder.py -I eth0 -wFb command:

The switches used in the snippet provide the following functions:
-
- -I: Specifies the interface to use
- -w: Enables the WPAD rogue proxy server
- -F: Forces NTLM authentication on wpad.dat file retrieve
- -b: Is used to return basic HTTP authentication
- When the victim attempts to browse or access any local resources on the network, the following login window will appear:
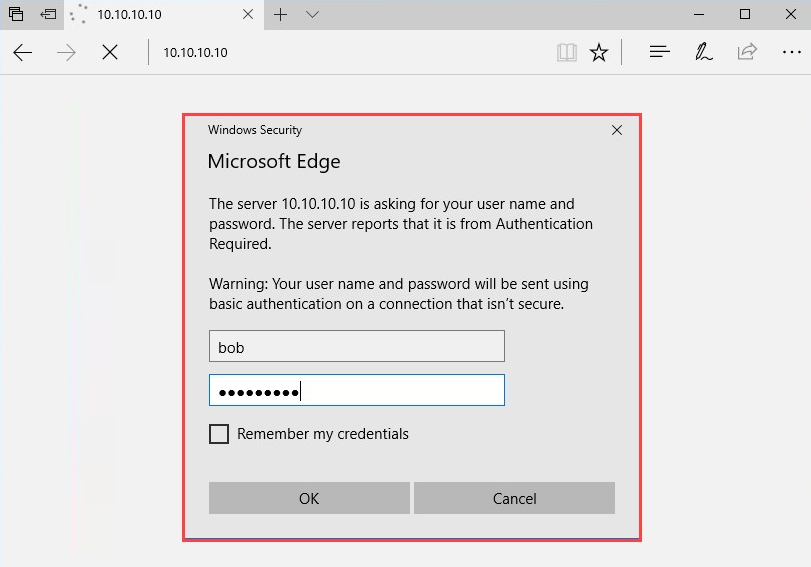
- Once the victim enters their user credentials, Responder will display them in plaintext, as shown in the following screenshot.
Just as a reminder, all logs generated and data captured by Responder are stored in the /usr/share/responder/logs directory. Now, you are able to capture employees' user credentials by exploiting WPAD on a corporate network:

In the next section, we will learn about Wireshark.
