So far, we have been able to gather basic details about a target. We can use Nmap to help users determine the operating system, the operating system version, and the service versions of any running applications on a target.
Using the -A operator will initiate an aggressive scan, -O will profile the operating system, and -sV will identify service versions.
Using the nmap -A -O -sV target command on our Metasploitable VM as our target system, we will be able to obtain much more meaningful information about the target.
As you can see in the following snippet, for each port that is open, Nmap has identified a particular service operating on the port, and we were able to retrieve the application service version details as well:
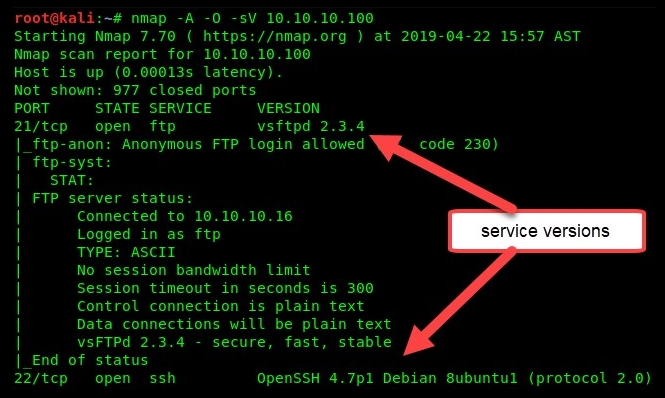
Scrolling down a bit more on the output, we can see that, by using the -O parameter, Nmap was able to determine the type of operating system:
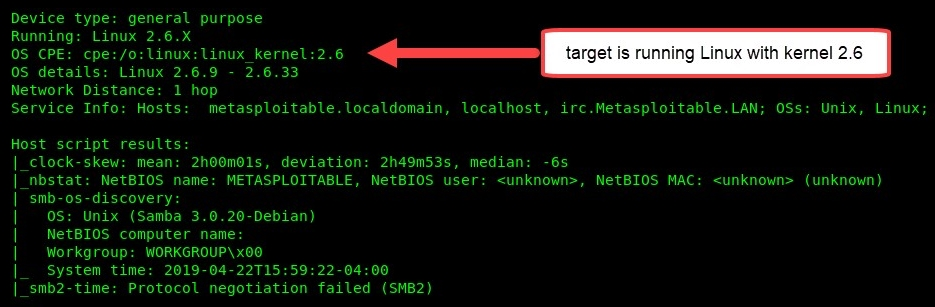
At this point, we have a much better idea of our target, the Metasploitable VM. We know all of the open ports, services, and service versions that are currently running, as well as the operating system.
Nmap is awesome, isn't it? Let's learn how to use Nmap to scan a device that has ICMP disabled.
