Whenever a packet is sent from one device to another, the source IP address is included within the header of the packet. This is the default behavior of the TCP/IP stack; all address details must be included within all packets that need to traverse a network. In performing a network scan on a target, our source IP address is included within all packets that our machine, Kali Linux, sends to the target.
Nmap has the capability of using decoys to trick the target into believing that the network scans are originating from multiple sources rather than a single source IP address. The -D operator is followed by random IP addresses, which are the decoys. Let's assume we want to scan an IP address, 10.10.10.100, and set three decoys: 10.10.10.14, 10.10.10.15, and 10.10.10.19. We can use the following command:
nmap -sS 10.10.10.100 –D 10.10.10.14, 10.10.10.15, 10.10.10.19
Observing the following Wireshark capture, we can see that packets containing both our source IP address and the decoys' IP addresses were used during the port scan on our target:
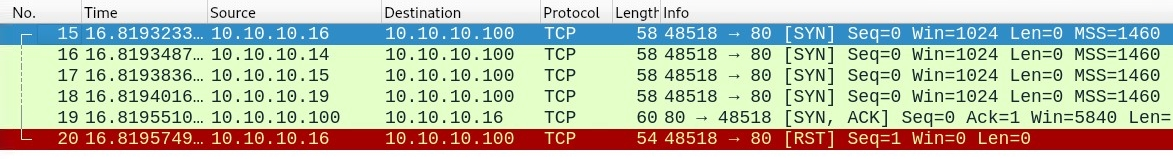
However, an RST packet is sent from the actual source address. Additionally, we can use other operators such as --spoof-mac to spoof the source MAC address.
In the next section, we will learn how to evade firewall detection while performing a network scan using Nmap.
