In this section, we will perform session hijacking on a target machine on our network. To perform this attack, we will combine a few other techniques to ensure that it's successful. Whenever a user visits a website, the web server sends a cookie to the web browser. The cookie is used to monitor the user's activities and provide a better user experience by tracking items in a shopping cart, maintaining persistent login while browsing other areas of a website, and so on.
Session hijacking allows an attacker or penetration tester to capture and take over (hijack) another user's sessions while the victim is logged into a website. Session hijacking allows the penetration tester to capture the session token/key, which is then used to gain unauthorized access to information and resources on a system. For example, capturing the session of a user who is logged into their online banking portal can allow the attacker to access the victim's user account without having to enter the victim's user credentials, as they can simply provide the cookie data to the website/online portal.
Before we begin, we will be using the following topology in our lab network to complete our exercise:

To ensure that you complete this exercise successfully, use the following instructions:
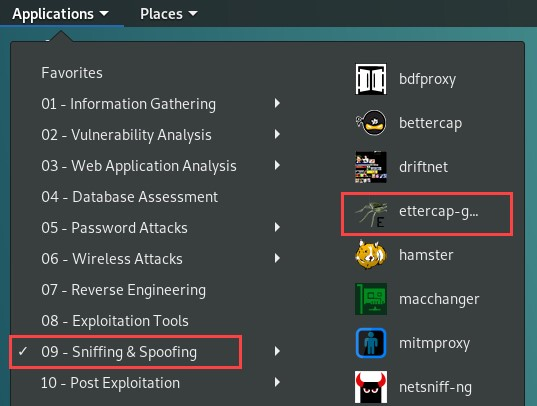
- Set up an MITM attack using Ettercap-Graphical with Kali Linux. To perform this task, navigate to Applications | 09 – Sniffing & Spoofing | ettercap-graphical as shown here:
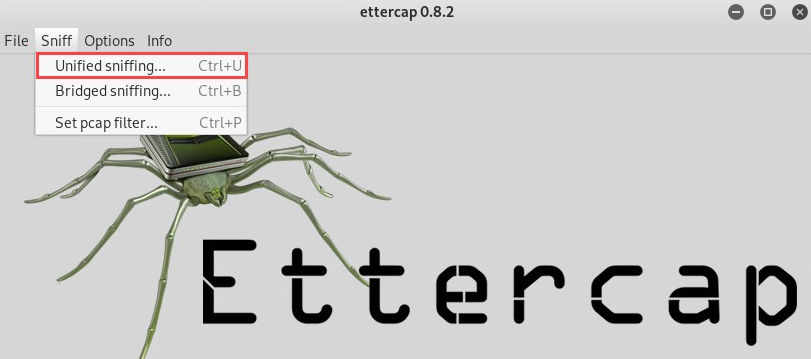
- Once Ettercap has opened, click on Sniff | Unified sniffing:
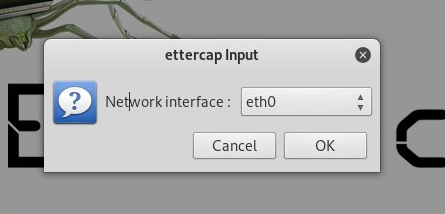
- A small popup will appear. Select your Network interface: eth0 and click OK:
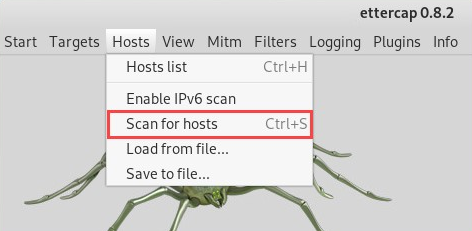
- Scan for all host devices on your network by navigating to Hosts | Scan for hosts:
- Once the scan has been completed, click on Hosts | Hosts list to view a list of targets on your network. Select your target and click on Add to Target 1:
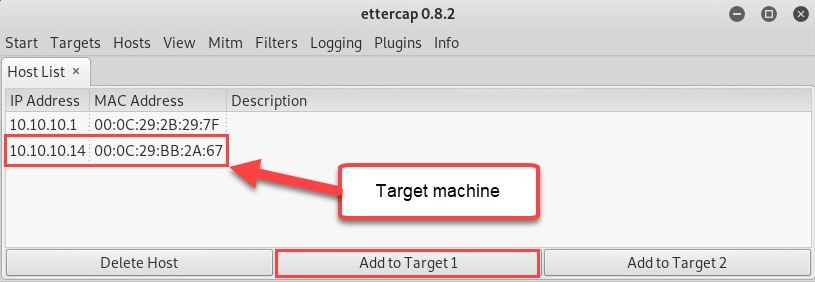
- Once the target has been added successfully, enable ARP poisoning on Ettercap by navigating to Mitm | ARP poisoning:

- A pop-up window will appear. Select Sniff remote connections. and click on OK:

- Next, click on Start | Start sniffing to enable the MITM attack:

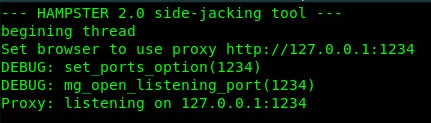
- Next, we are going to use the Hamster tool to help us manipulate the data. To open Hamster, navigate to Applications | 09 – Sniffing & Spoofing | hamster:

Hamster will open a command-line interface on a new Terminal window and provide the URL, http://127.0.0.1:1234, which is used to view the session information:
- Next, we will use Ferret to capture the session cookies between the victim and the data's destination. By default, Kali Linux does not have Ferret installed; also, Ferret is a 32-bit tool. To install Ferret on Kali Linux, use the following command:
dpkg --add-architecture i386 && apt-get update && apt-get install ferret-sidejack:i386
Once the installation has completed successfully, navigate to Applications | 09 – Sniffing & Spoofing | ferret:
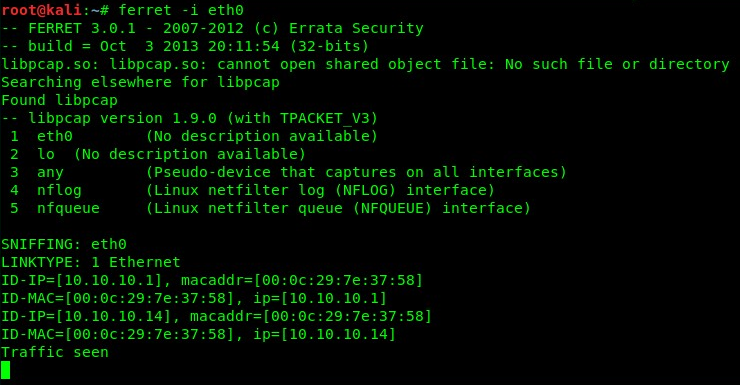
- Use the ferret -i eth0 command to capture cookies on the Ethernet interface:
- Open the web browser on Kali Linux and enter http://127.0.0.1:1234 to access the Hamster proxy interface. Click on adapters:

- Select the eth0 adapter and click Submit Query:
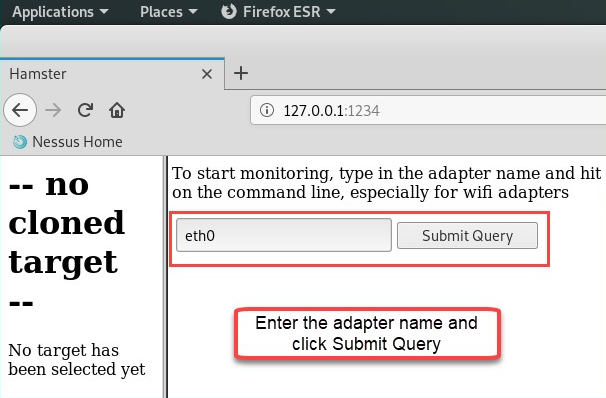
- Go to the victim's machine and, using the web browser, enter the IP address of Metasploitable. Next, click on Damn Vulnerable Web Application (DVWA). Then, log in using the username (admin), and the password (password), to generate some traffic between the victim machine and another system.
- On your Kali Linux machine, refresh the Hamster web page. You should now see the victim's IP address appear. Click on the victim's IP address to get more information:
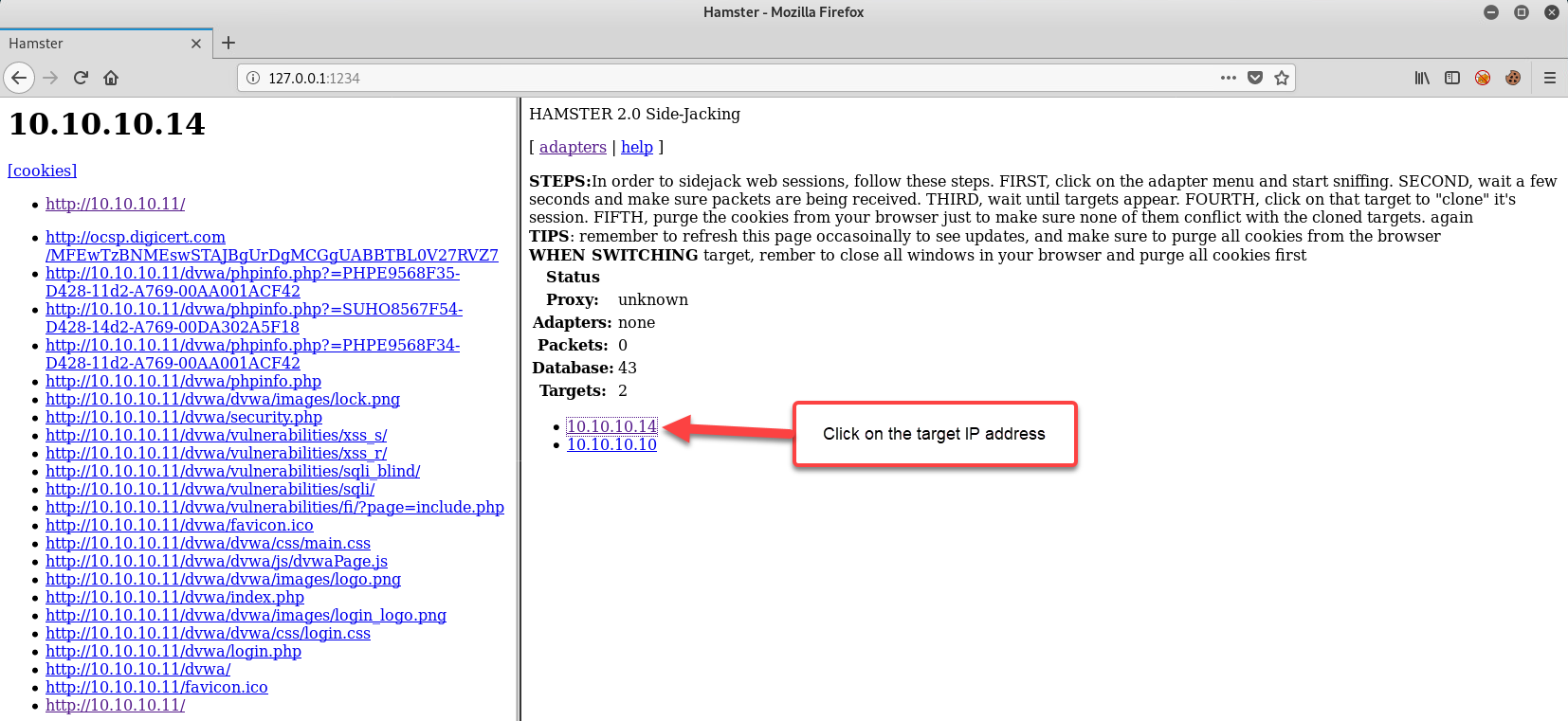
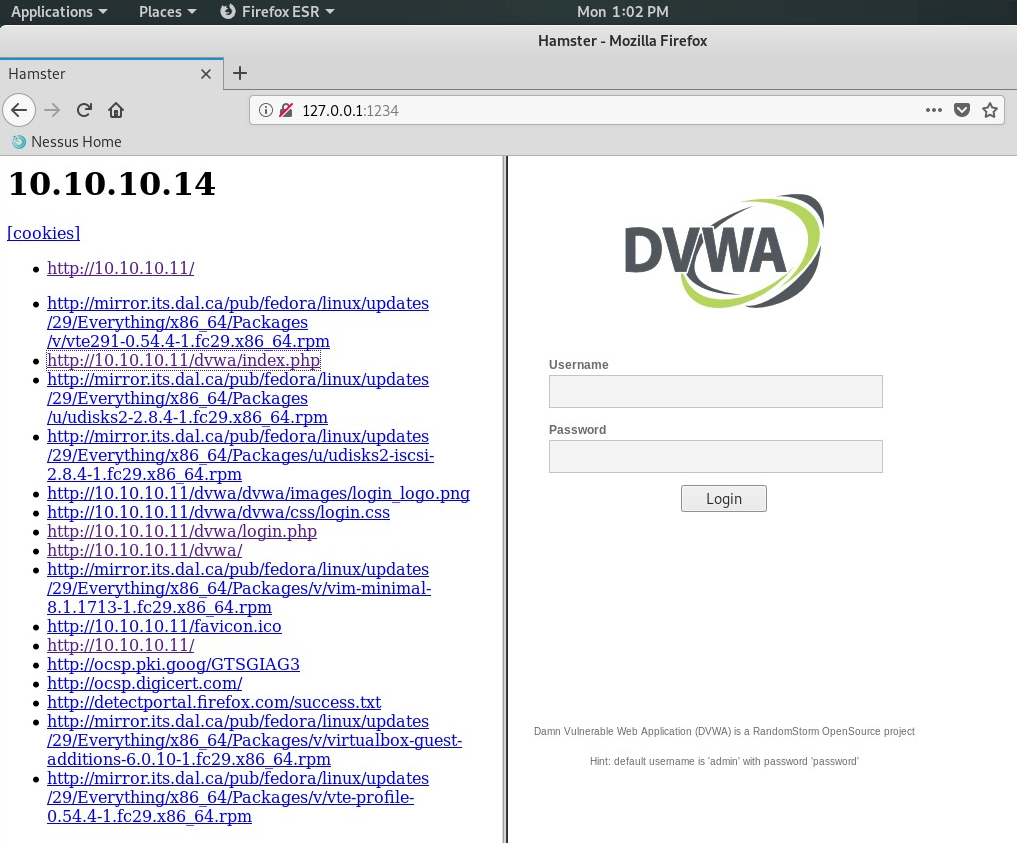
- Clicking on any of the URLs on the left-hand column will provide an image of what the victim might have seen on their web browser:
- To view a list of cookie/session details, open a new tab on your web browser and enter the URL shown here:
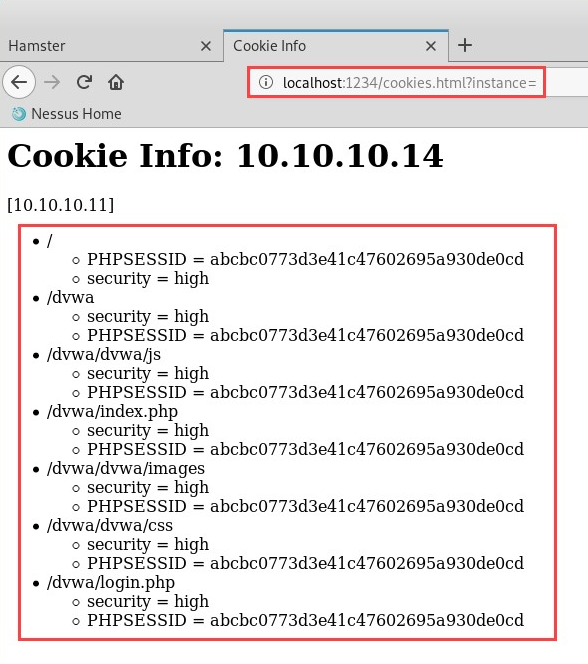
We were able to capture the session cookies for the transactions between the victim's machine and the web server. Having completed this exercise, you are now able to perform cookie stealing/session hijacking attacks.
Now that you have completed this exercise, you have the skills required to perform a session hijacking attack on any network. In the next section, we will cover Dynamic Host Configuration Protocol (DHCP) attacks.
