In this exercise, we will be using the OWASP BWA virtual machine to demonstrate bypassing authentication using SQL injection. To start, power on the OWASP BWA virtual machine. After a few minutes, the virtual machine will provide you with its IP address.
Head on over to your Kali Linux (attacker) machine and follow these steps:
- Enter the IP address of the OWASP BWA virtual machine in the web browser of Kali Linux.
- Click on the OWASP Mutillidae II application, as follows:
- Navigate to the following page: OWASP 2013 | A2 - Broken Authentication and Session Management | Authentication Bypass | Via SQL Injection | Login:

- Enter any one of the following characters in the Username field:
- '
- /
- --
- .
If an error occurs, examine the message produced by the server.
When we run this, something similar to the following error should appear. If you look closely, you can see the query that was used between the web server application and the database, SELECT username FROM accounts WHERE username= ' ' ' ;, as shown here:
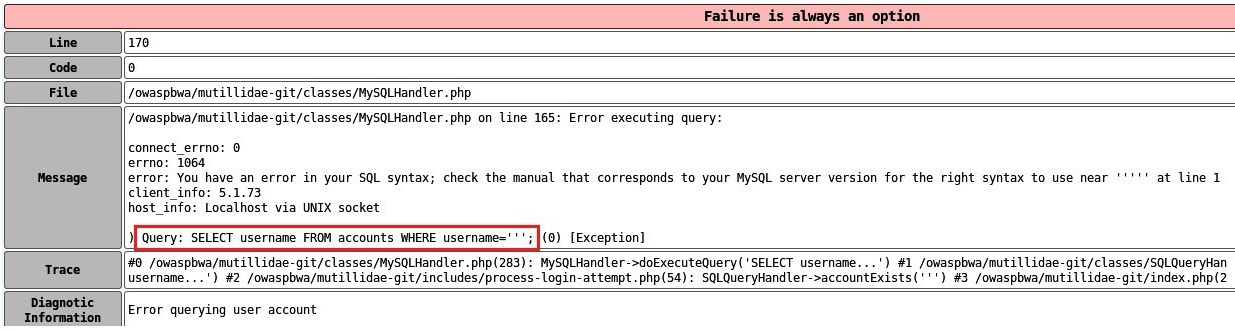
The following can be determined from the SQL query:
-
- The SELECT statement is used to retrieve information from a relational database. Therefore, the statement begins by saying: SELECT the username column from the table.
- The FROM statement is used to specify the name of the table. In the statement, we are specifying the accounts table.
- The WHERE statement is used to specify a field within the table. The query indicates the field(s) that has (have) a value equal to ' (a single quotation mark). The = (equals) parameter allows us to ensure a specific match in our query.
- ; is used to end a SQL statement.
- When combined, the statement reads as follows: Query the username column within the accounts table, and search for any username that is ' (single quotation mark).
- Let's attempt to combine some statements. Use the ' or 1=1 -- (there is a space after --) statement in the Username field, and then click on Login:

The statement chooses the first record within the table and returns it. Upon checking the login status, we can see that we are now logged in as admin. This means the first record is admin:

The statement chooses the first record in the table and returns the value, which is admin.
- Let's try another user and modify our code a bit. We will attempt to log in as the user john. Insert the username john for the username field and the following SQL command for the password field:
' or (1=1 and username = 'john') --
Ensure that there is a space after the double hyphens (--) and hit Login to execute the commands. The following screenshot shows that we are able to successfully log in as the user john:

Those are some techniques you can use to bypass authentication using SQL injection attacks on a web server. In the next section, we will cover SQL injection vulnerabilities and exploitation.
