As mentioned previously, the Metasploitable virtual machine was created by the team at Rapid7 (www.rapid7.com) for the purpose of cybersecurity awareness and training. In this section, I'll walk you through the steps involved in setting up a Metasploitable virtual machine in your lab:
- Firstly, you need to download the virtual image file from https://sourceforge.net/projects/metasploitable/files/Metasploitable2/. Once downloaded to your computer, extract the ZIP folder to view the contents.
- Next, right-click on the following highlighted file, and either choose the option to import or open with a hypervisor of your choice:
- Once the importing process has finished, the new virtual machine will appear in your library in the hypervisor (VirtualBox or VMware). Ensure that the network adapter is set to Custom (VMnet1), just like the virtual network for our lab is:

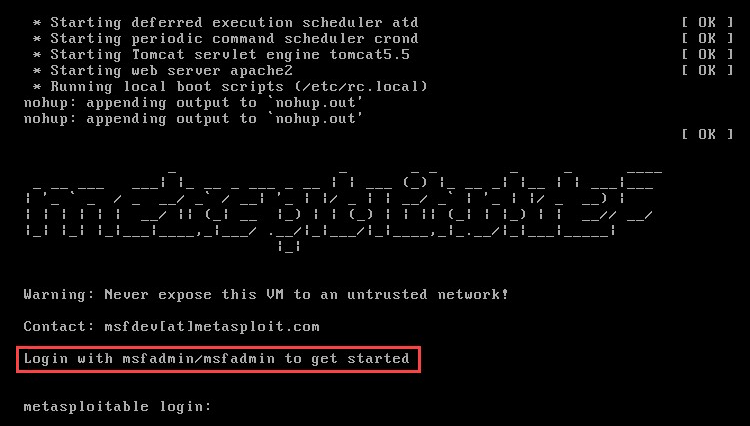
- To test the virtual machine, power it on, and let it boot. Once the boot process is complete, you'll see that the login credentials (username/password) are part of the system banner, msfadmin/msfadmin:
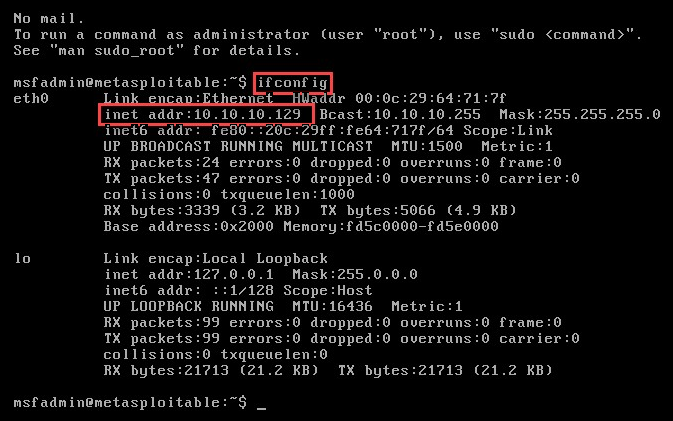
- Log in to the virtual machine using the credentials, and use the ifconfig command to verify that it has a valid IP address:
You now have a vulnerable Linux-based operating system in your lab. It's always recommended to have a mixture of various target operating systems in a lab when practicing penetration testing techniques and honing your skills. This method allows you to learn how to perform attacks on a variety of different targets, which is important since a corporate network usually has a blend of many different devices and operating systems. You don't want to be in a penetration test engagement where the target organization has mostly Linux devices but you're skills are geared toward only Windows-based systems; this would be a bad sign for you as a penetration tester! Therefore, emulating a corporate network in a lab as closely as possible will help you to improve your skills.
