Organizations usually implement virtual local area networks (VLANs) to segment and improve the performance of their network infrastructure while improving security. When configuring VLANs, there are two main ports that we are concerned with: the access port and the trunk port.
Access ports are those that are configured to connect the end device to the switch. These ports only allow one data VLAN and an additional voice VLAN. When configuring an access port, the VLAN ID is usually statically configured as an access port on a switch.
For multiple VLANs to communicate over a network, trunk ports need to be configured between switches. Trunk ports allow multiple VLANs to pass traffic simultaneously. Trunk ports are configured between switches and are configured between a switch and a router to implement inter-VLAN routing, which allows one VLAN to communicate with another VLAN.
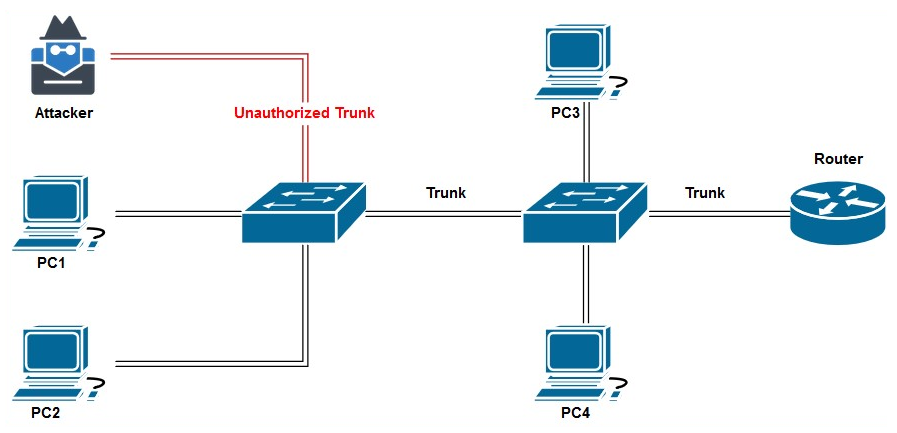
There are many times when IT professionals do not configure networking devices properly. A penetration tester can exploit this vulnerability and attempt to perform a VLAN hopping attack. Once successful, the attacker machine will be able to access all available VLANs and perform MITM attacks. The following diagram shows an attacker who has successfully enabled an unauthorized trunk:
Yersinia on Kali Linux allows an attacker to perform various types of layer 2 attacks on a network to take advantage of security misconfigurations and weaknesses. To open yersinia, execute the following command:
yersinia -G
The graphical user interface will appear on your desktop. To launch a VLAN hopping attack, execute the following steps:
- Click the Launch attack button.
- A new window will appear. Click the DTP tab and select the enabling trunking radio button, as shown in the following screenshot:

- When you're ready, click OK to begin performing a VLAN hopping attack on the network.
Having completed this section, you are now able to perform VLAN hopping attacks using Kali Linux.
