Microsoft's RDP provides a GUI for the user to establish a connection to a Windows-based system over the network. Quite often, system administrators enable the RDP service on their client and server machines in an organization for easy access. With RDP enabled on a device, a system administrator does not need to physically go to the geographic location of a system to check its configurations or make adjustments to the operating system. All they have to do is simply log on using RDP. This protocol makes the job of IT professionals a bit easier and more efficient.
The protocol was designed for remote access. However, as a penetration tester, we can take advantage of systems that have RDP enabled by attempting to discover valid user credentials for target systems. Let's get started:
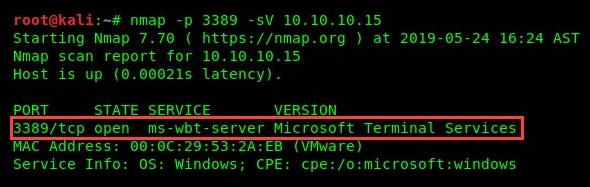
- To begin, we can use Nmap to scan a network while searching for any device that has RDP enabled. RDP uses port 3389 on Windows, and so we can use the following Nmap command to scan a target:
nmap -p 3389 -sV <target IP address>
The following screenshot indicates a system that has port 3389 open and is running Microsoft Terminal Services:
- Now that we have found a suitable target, we can perform a dictionary attack on the live target. Using Ncrack (an offline password-cracking tool), we can use a list of possible usernames (usernames.txt) and passwords (custom_list.txt), as shown in the following screenshot:

The following are descriptions of each of the switches used in the preceding snippet:
-
- -v: Increases the verbosity of the output on the Terminal.
- -T (0-5): Adjusts the timing of the attack. The higher the number, the faster the attack is.
- -U: Allows you to specify a list of usernames.
- --user: Allows you to specify usernames, each separated by a comma.
- -P: Allows you to specify a list of passwords.
- --pass: Allows you to specify passwords, each separated by a comma.
- service://host: Ncrack uses this format to specify a service and a target device.
As you saw, Ncrack was able to find a valid username and password combination for the target (10.10.10.19). Thus, having obtained the user's credentials, it's now simple to use them to our advantage.
- At this point, once you've obtained a valid user account, the next step is to actually log in to the target using the RDP and other network services (Telnet, SSH, VNC, and so on) you found running on the target system.
Another online password cracking tool we could use is Hydra. To use Hydra to perform the same task we just did with Ncrack, you can execute the following command:
hydra -V -f -L usernames.txt -P custom_list.txt rdp://10.10.10.19
Upon receiving a meterpreter shell in Metasploit, the following are some useful commands to help you capture keystrokes and the victim's screen:
- screenshare: This command is used to watch the remote victim's desktop in real time.
- screenshot: Takes a picture of the victim's desktop.
- keyscan_start: Starts keylogging using Meterpreter.
- keyscan_stop: Stops keylogging.
- keyscan_dump: Produces a dump of the keystrokes captured.
The following screenshot shows a live screen view of a victim's desktop after executing the screenshare command in Meterpreter:
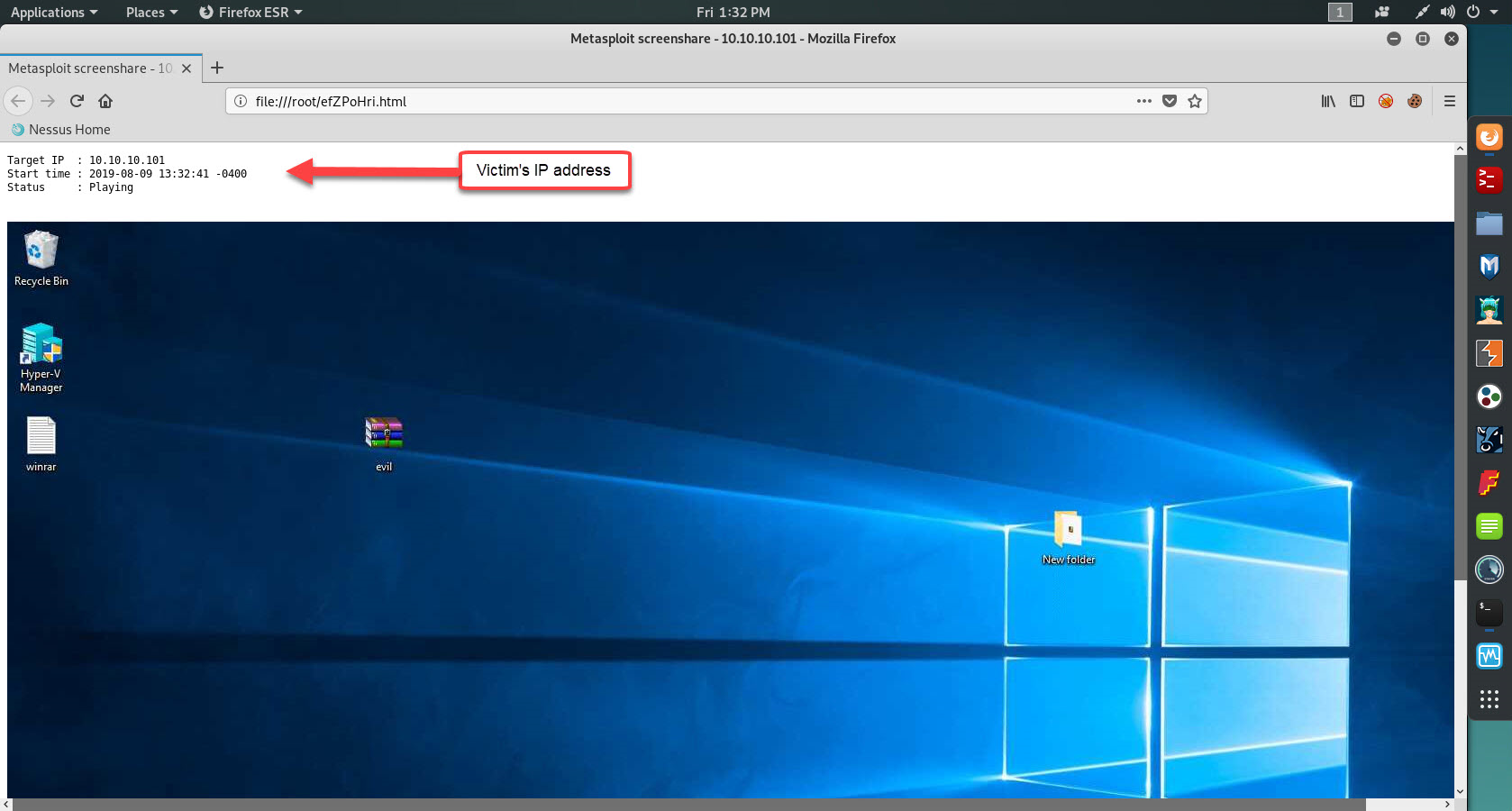
As you can see, it's quite scary what a real hacker can do once they have gained access to a network or system.
You're now able to detect and exploit the EternalBlue vulnerability in the Windows operating system. Next, we'll take a look at leveraging user credentials for our benefit.
