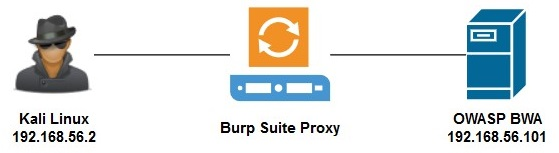
In this exercise, we will attempt to discover whether SQL injection is possible with POST. The POST method is used to send data to a web server. This method is not like the GET method, which is used to retrieve data or a resource. We will be using the following topology to complete this exercise:
To start detecting SQL injections with POST, use the following instructions:
- Enable Burp Proxy on your Kali Linux machine and confirm that your web browser proxy settings are correct. If you are unsure, please refer to Chapter 7, Working with Vulnerability Scanners, specifically the Burp Suite section, which contains all the details you need to configure Burp Suite on your Kali Linux machine.
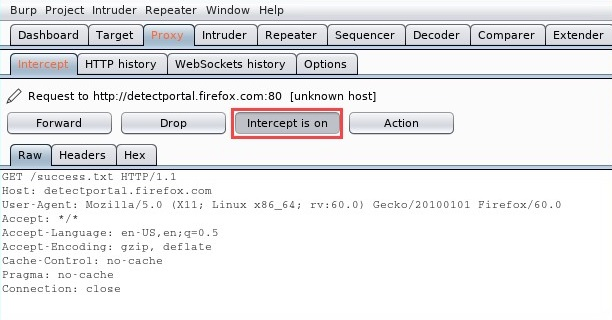
- Ensure that Intercept is enabled on Burp Suite, as shown here:
- Open your web browser on Kali Linux and enter the OWASP BWA IP address in the address bar.
- Click on bWAPP as shown in the following screenshot. Log in to the bWAPP portal with the credentials bee (username) and bug (password). Please note that these are the default user credentials for the bWAPP virtual machine:

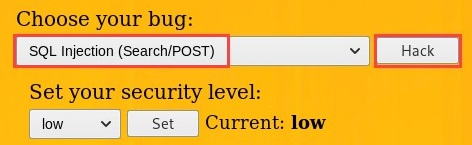
- In the top-right corner, use the drop-down menu to select SQL Injection (Search/POST), and then click on Hack to load the vulnerability:
- Enter a word in the search field and click on Search to submit (post) data:

The database will respond by stating whether a movie was found.
- On Burp Suite, select the Target | Site map tab to view all the GET and POST messages between your web browser on Kali Linux and the OWASP BWA web server.
- Select the most recent POST message, which should contain the search you just performed:

The following shows the content of this POST message:

- Right-click anywhere within the Raw content window and select the Save item option. Save the file on your desktop in Kali Linux as postdata.txt.
- Once the file has been saved successfully, let's use SQLmap to discover any SQL injection (SQLi) vulnerabilities in POST on the target server. Use the following command to perform this task:
sqlmap –r /root/Desktop/postdata.txt
- SQLmap will attempt to check any/all POST parameters and determine whether the application is vulnerable. The following shows a number of possible vulnerabilities:

In the preceding screenshot, SQLmap was able to notice that the 'title' parameter may be vulnerable and that the database may also be a MySQL platform. Additionally, the following is an example of an injectable parameter that has been found:
![]()
The preceding screenshot shows that SQLmap has determined that the 'title' parameter is also vulnerable to SQL injection attacks. Lastly, the following are SQLmap payloads:
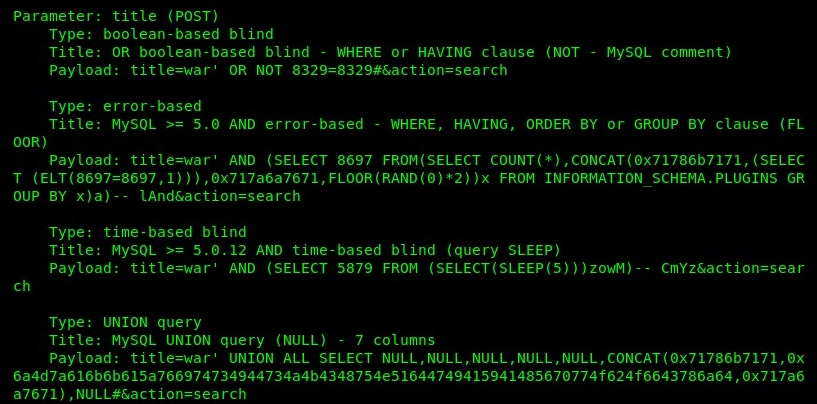
Here, SQLmap provides us with a bit of a summary of what has been tested, how it was tested, and the results. With the information that SQLmap has given us, we know exactly where the target website is vulnerable to SQLi attacks with POST and how to leverage weaknesses using specific payloads.
Having completed this exercise, you are now able to use Burp Suite and SQLmap to discover SQL injection vulnerabilities in POST messages.
In the next section, you will learn how to use the SQLmap tool to discover SQL injections.
