SMBmap is a popular and easy-to-use tool that is used to help us discover any SMB shares on a device and detect permissions on any shares found:
- Using the smbmap -H target syntax, we can attempt to perform a port scan, looking for ports that are used by the SMB service; in our target, it's 445 and it's open:

- SMBmap will attempt to establish a session between the attacker machine and the target on port 445 to enumerate any share drives and folders. On our target (Metasploitable), there's the tmp folder, which gives us read and write permissions.
- Using the smbmap -H 10.10.10.100 -r tmp command, we will be able to list the contents of the directory specified. In our example, we are listing the content of the tmp folder, as shown in the following screenshot:
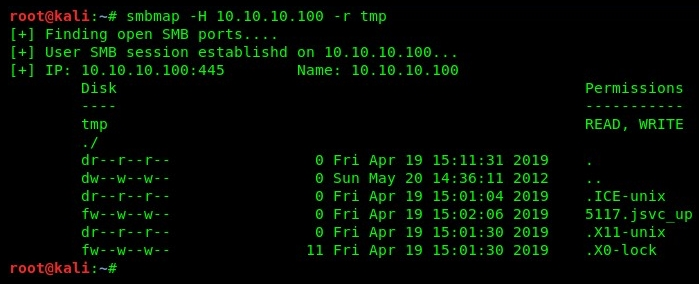
SMBmap is an excellent tool for enumerating SMB shares on target devices; however, it's always good to have another tool available in your arsenal. Other tools include SMBlookup, SMBclient, and Nmap.
SMBclient is another handy tool and works in a similar fashion to SMBmap. To enumerate SMB services on a target, we can use the smbclient -L //target command:
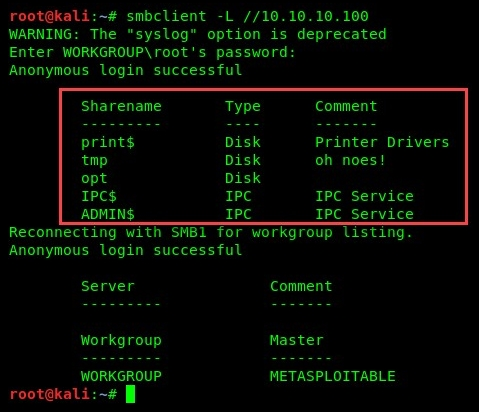
SMBclient will attempt to extract any shares on the target device, as seen in the previous screenshot. Further information on SMBclient can be found at: https://www.samba.org/samba/docs/current/man-html/smbclient.1.html.
Having completed this section, you have gained the skills to use both SMBmap and SMBclient to perform SMB enumeration on a target. In the next section, we will briefly discuss another popular tool for SMB enumeration, Enum4linux.
