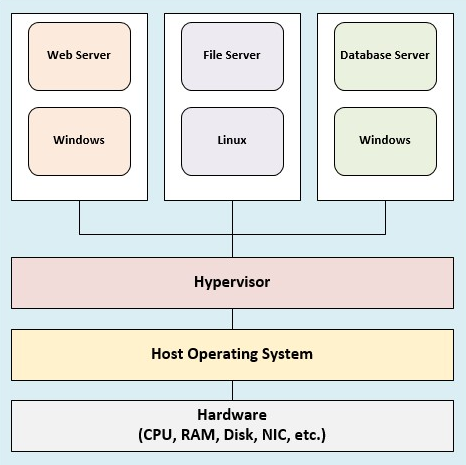
In a type 2 hypervisor deployment model, the hypervisor application is installed on top of a host operating system rather than on the hardware components directly. Examples of host operating systems include Microsoft Windows, the Apple macOS, and various flavors of Linux. The hypervisor does not have direct access to the hardware resources on the local system, as it would in the type 1 deployment model. Instead, the hypervisor in a type 2 deployment interfaces with the host operating system to access whatever resources are available. The host operating system usually requires a certain amount of resources, such as CPU and RAM utilization, in order to function optimally, and the remainder is then provided to the type 2 hypervisor for the guest virtual machines.
The following is a diagram illustrating how each component interfaces with the other on a single system, such as a desktop or laptop computer. Looking closely, each virtual machine has indirect access to the resources (CPU, memory, and so on). The operating system will have priority when it comes to hardware resources, and what is left is then made available to the running virtual machines:
The following is a brief list of type 2 hypervisors. Please note that some are free while others are commercial:
- Microsoft Virtual PC (free)
- Oracle VM VirtualBox (free)
- VMware Player (free)
- VMware Workstation Pro (commercial)
- VMware Fusion (commercial)
- Parallels Desktop for Mac (commercial)
You may be wondering which hypervisor is the better option—type 1 or type 2? Honestly, it really depends on your situation. Personally, I have a type 2 hypervisor installed on my laptop with a few virtual machines, which I use for training and other situations at remote locations. While at home, I have a type 1 hypervisor installed on an Intel NUC in my home lab, which has multiple virtual machines, each for a different purpose.
Now that you have a better idea of the concepts of hypervisors, let's learn about the features of a hypervisor, as that will help us to build a virtual network for creating our penetration testing lab.
