A CSRF attack is a bit similar to an XSS attack. Let's use an analogy to simplify our explanation of CSRF attacks. Imagine a user, Bob, who opens his web browser and logs in to his banking customer portal to perform some online transactions on his account. Bob has used his user credentials on his bank's web portal; the web application/server verifies that the user is Bob and automatically trusts his computer as the device communicating with the web server.
However, Bob also opens a new tab in the same browser to visit another website while maintaining an active session with the bank's web portal (trusted site). Bob doesn't suspect that the new website he visits contains malicious code, which is then executed in the background on Bob's machine:
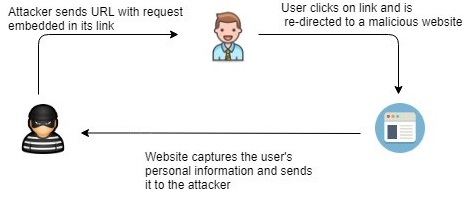
The malicious code then injects an HTTP request into the trusted site from Bob's machine. In this way, the attacker is able to capture Bob's user credentials and session information. Additionally, the malicious link can cause Bob's machine to perform malicious actions on the trusted site as well.
In the next section, we will cover the essentials of SQL injection (SQLi) attacks.
