By default, Nmap establishes a TCP three-way handshake on any open TCP ports found. After the handshake has been established, the messages are exchanged. The following snippet displays the handshake process, where Host A wants to communicate with Host B:
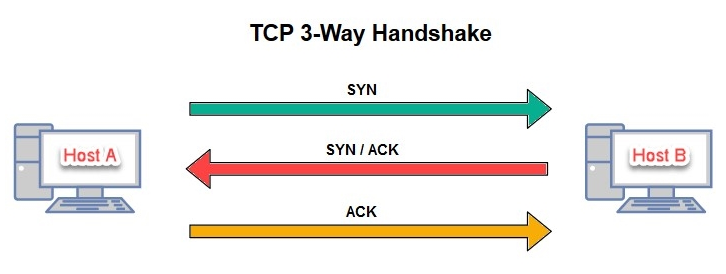
During a penetration test, we need to remain as stealthy as possible on the network. This creates the effect of an actual hacker attempting to compromise the system/network without being caught by the organization's security controls and systems. By establishing a TCP three-way handshake with our target devices, we are making ourselves known to the target.
Therefore, we are going to perform a stealth scan (half-open) using Nmap. A stealth scan does not establish a full TCP handshake with the target:
- The attacker machine tricks the target by sending a TCP SYN packet to a particular port on the target if the port is open on the target.
- A TCP SYN/ACK packet is returned to the attacker machine.
- Lastly, the attacker sends a TCP RST packet to reset the connection state on the target:

In our exercise, we are going to probe port 80 on our Metasploitable VM using stealth scanning with Nmap. Using the -sS operator to indicate a stealth scan, and with the -p operator scanning (probing) a particular port, we can execute the nmap -sS -p 80 10.10.10.100 command on our Kali Linux machine:

Using Wireshark, we are able to see the flow of packets between our Kali Linux machine and the target. Packet number 18 indicates that an [SYN] packet was sent to the Metasploitable VM, packet number 19 indicates that an [SYN, ACK] packet was returned to the Kali Linux machine, and finally, packet number 20 indicates that our Kali Linux machine sent an [RST] packet to reset the connection:
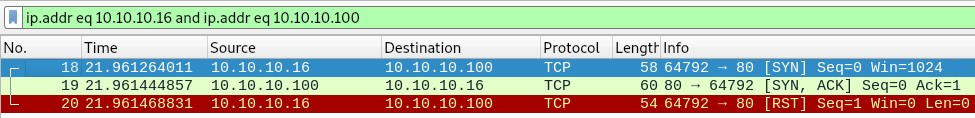
The final result is that we were able to successfully probe a given port on a target system and did not establish a network session between our machine and the target.
There are many services and protocols that use UDP as a preferred transportation method. UDP applications do not respond to a typical port scan by default. Whenever you perform a network/port scan using Nmap, the scanning engine searches for open TCP ports by default; this means UDP ports are usually missed in the results. In the next section, we'll take a look at performing a UDP port scan.
