Whenever a client device, such as a laptop or smartphone, is attempting to create an association with a password-protected wireless network, the user will need to provide the correct passphrase. If the user provides the correct passphrase, the device will be authenticated on the network and will be able to access any resources available.
In a deauthentication attack, the attacker, or penetration tester, is attempting to knock (kick) every associated device off a wireless AP. This attack is executed where the attacker machine is not connected (associated) in any way to the target wireless AP or network.
For the attacker machine to send a deauthentication frame to the wireless AP, a reason code is inserted within the body of the frame. The codes are used to inform the access point or wireless router of a change on the network. The reason code will indicate one of the following:
- Code 2: Previous authentication no longer valid
- Code 3: Deauthentication leaving
This will create the effect of each client being deauthenticated from the targeted AP. The following is an illustration of the attack on a network:
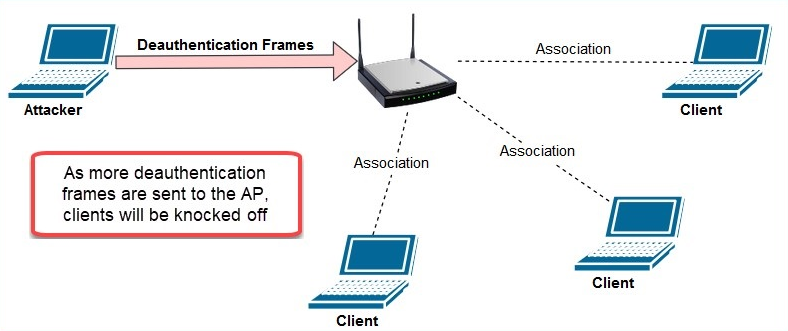
To launch a deauthentication attack, perform the following steps:
- Enable monitor mode on your wireless adapter.
- Use the airodump-ng wlan0mon command to discover your target's BSSID address. The BSSID will be used to launch our attack specifically toward a particular AP.
- Once the target AP has been discovered, take note of its BSSID and operating channel, and then terminate the scanning of nearby APs by using Ctrl + C.
- Narrow your scope on wireless monitoring to the specific target AP just by using the following syntax: airodump-ng --bssid <bssid value> -c <channel #> wlan0mon. This current Terminal window will be used to monitor the progress of our attack.
- Open a new Terminal window. This window will be used to launch the attack using the aireplay-ng tool. The aireplay-ng -0 0 -a <BSSID> wlan0mon command will send a continuous stream of deauthentication frames to the target AP.
Your results should be similar to the following screenshot:
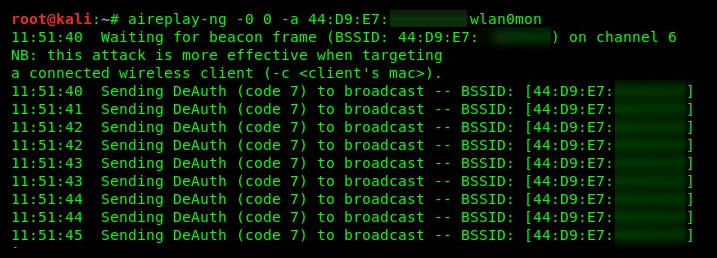
In the screenshot, we can see that aireplay-ng is sending a continuous stream of deauthentication frames to our targeted access point.
During the attack, switch back to the first Terminal window where you are monitoring your target network. Soon, you'll see that the clients (stations) are being disconnected and, eventually, the WPA/WPA2 handshake will be captured. You will notice on your Terminal with airodump-ng that the WPA handshake value will appear in the top-right corner of the window. This is an indication that the WPA/WPA2 handshake has been captured. In the next chapter, we will perform password cracking on a wireless network.
Additionally, if you would like to deauthenticate a specific client (station) from an AP, the following command will allow this action:
aireplay-ng -0 0 -a <target's bssid> -c <client's mac addr> wlan0mon
The following are descriptions of each parameter we used:
- -0: This indicates that it's a deauthentication attack.
- 0: This specifies the number of frames to inject. Using 0 will create a continuous attack; if you specify 2, only two deauthentication frames will be injected.
- -c: This allows you to specify the client's MAC address.
In the next section, we'll be creating a honeypot using Kali Linux and various wireless tools.
