SPAN allows a switch to create a copy of traffic on one or more ports and send the same copy out of another port. This configuration is usually done when a network security administrator wants to connect a protocol analyzer (sniffer) or an intrusion detection system (IDS) to the network to monitor for any security threats:

In the diagram, the attacker machine (running Wireshark) is connected to the Fast Ethernet 0/1 interface on a Cisco IOS 2960 switch, while the other devices are connected to the same network segment. Let's say we would like to get a copy of all traffic flowing between the Fast Ethernet 0/2, Fast Ethernet 0/3, and Fast Ethernet 0/4 ports.
To perform this task of configuring a SPAN port on a Cisco IOS switch, use the following guidelines:
- We can use the following command to send the output to Fast Ethernet 0/1:
Switch (config)# monitor session 1 source interface fastethernet 0/2
Switch (config)# monitor session 1 source interface fastethernet 0/3
Switch (config)# monitor session 1 source interface fastethernet 0/4
Switch (config)# monitor session 1 destination interface fastethernet 0/1
- To verify the configurations, use the show monitor command on the switch:
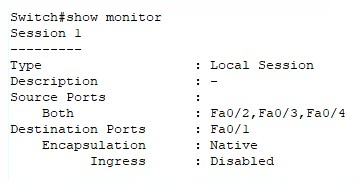
The output shows us that the source ports (used for monitoring network traffic) and destination ports are configured properly. Once we have enabled Wireshark on our attacker machine to start capturing on our local interface, eth0, all network packets will be shown live on the Wireshark user interface.
Having completed this section, you are now able to configure a SPAN port on a Cisco IOS switch. In the next section, we will dive into configuring Wireshark to sniff network traffic.
