Now that we have obtained user credentials for a target Microsoft Windows system, let's attempt to connect remotely. For this exercise, we are going to use the rdesktop client, which is already pre-installed within Kali Linux. Let's get started:
rdesktop is an open source protocol that's used for remote administration, similarly to Microsoft's RDP.
- To use rdesktop, open a new Terminal window and use the following syntax:
rdesktop -u <username> -p <password> <target's IP address>
The following snippet is an example of using the rdesktop tool with all the necessary details:
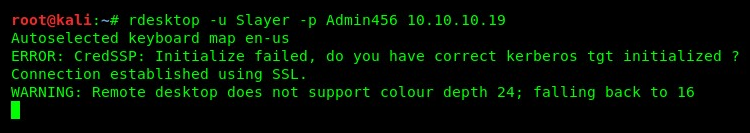
- Once you've executed the command, rdesktop will attempt to establish a remote connection to the target device. Once successful, rdesktop will provide a new window with the target's user interface, as shown in the following screenshot:
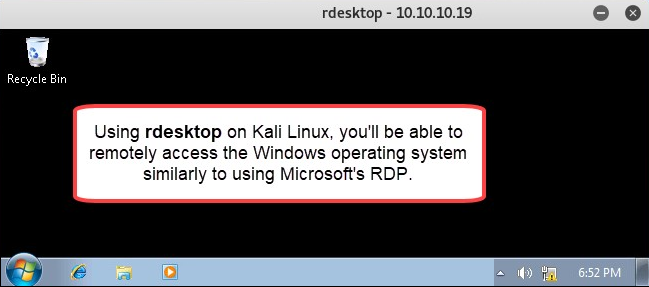
At this point, we have successfully gained entry to the target operating system and have control over it.
If your attacker system does not have the rdesktop tool, it can be found at its official GitHub repository: https://github.com/rdesktop/rdesktop. For further information on rdesktop, please go to its official website at www.rdesktop.org.
As you saw, we can simply use native tools within Kali Linux with the victim's credentials to access resources, systems, and networks during a penetration test. In the next section, we'll dive into network implants.
