Burp Suite (https://portswigger.net/burp) is a graphical user interface (GUI) web application vulnerability scanner that has the capability to identify over 100 generic vulnerabilities, such as all the vulnerabilities found in the OWASP top 10 list of critical web application security risks.
Burp Suite applications allow a penetration tester to intercept all HTTP and HTTPS requests and responses between the web server (web application) and the browser, via its HTTP proxy component. By intercepting web traffic, Burp Suite can test various types of vulnerabilities and attacks such as fuzzing, brute force password attacks, decoding, obtaining hidden URLs via spidering, and a lot more.
Before getting started with Burp Suite, ensure your OWASP Broken Web Applications (BWA) virtual machine (victim machine) is online and has received an IP address.
Once the OWASP BWA VM is online, you should be presented with the following screen; however, your IP address details may be different from what is shown:

On your Kali Linux machine, ensure there is end-to-end connectivity by pinging the OWASP BWA virtual machine. Once you've verified connectivity, it's time to open the Burp Suite application.
To complete this task, use the following instructions:
- Go to Applications | 03 – Web Application Analysis | Web Application Proxies | Burp Suite.
- Now the application is open, the wizard will ask whether you would like to create a Temporary project, a New project on disk, or Open existing project.
- Select Temporary project and click Next:

- The next window will ask whether Burp Suite should use the default setting or load configurations from a file. Select the Use Burp defaults option, and click Start Burp to launch the user dashboard:

Traffic sent between your web browser and the target web server is not monitored or intercepted by Burp Suite. Burp Suite contains an HTTP proxy that allows the application to intercept HTTP traffic between a web browser and a target web server. The web browser does not directly interact with the web server; traffic is sent from the web browser to the Burp Suite HTTP proxy, then the HTTP proxy forwards the traffic to the target web server and vice versa. The following is a diagram showing the flow of traffic between a web browser and a web server:

Burp Suite works as an intercepting proxy application. By default, Burp Suite is not able to intercept any traffic between our Kali Linux machine and the OWASP BWA virtual machine. To configure our web browser to work with Burp Suite, use the following instructions:
- Open Firefox and click on the menu icon | Preferences (Options).
- On the default tab, scroll down until you see the Network Proxy settings ( Network Settings) and click on Settings.
- Select Manual proxy configurations and use the configurations displayed in the next screenshot:
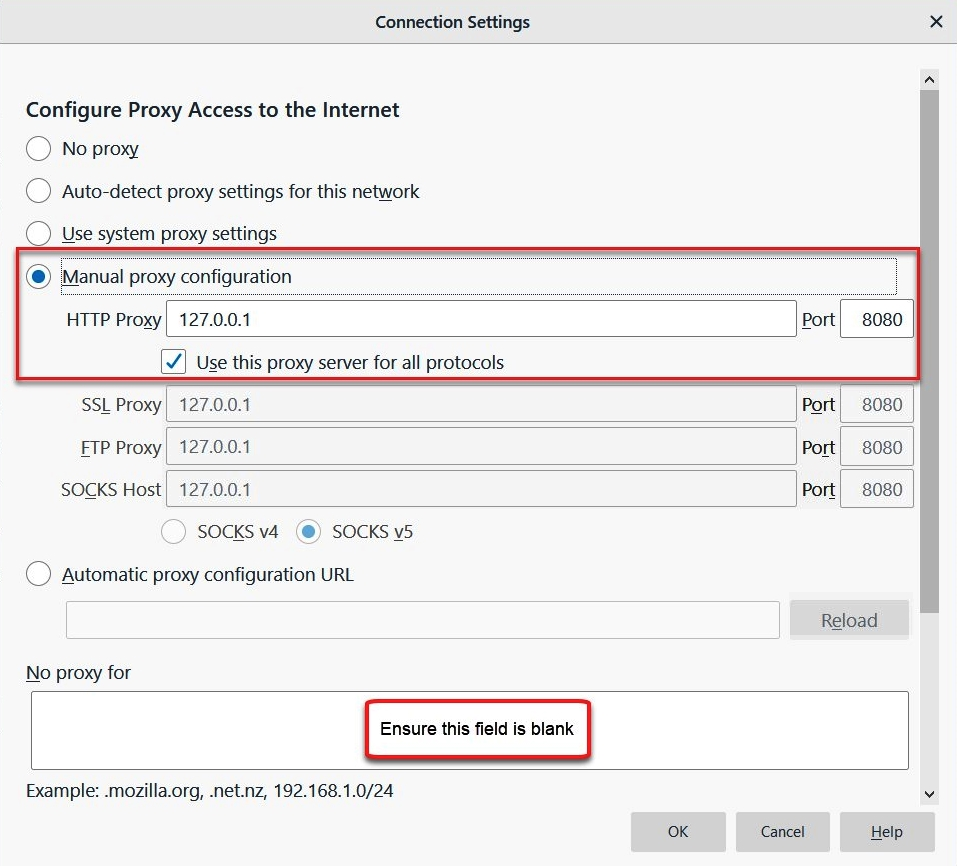
Ensure the No proxy for field is blank.
- Click on OK to save your settings in Firefox.
Now that we've configured our web browser to work with the Burp Suite HTTP proxy service, let's head back over to the Burp Suite application to allow the interception of traffic. To do so, follow these steps:
- Click on Proxy| Intercept, and click on the Intercept is on icon to toggle enable/disable:
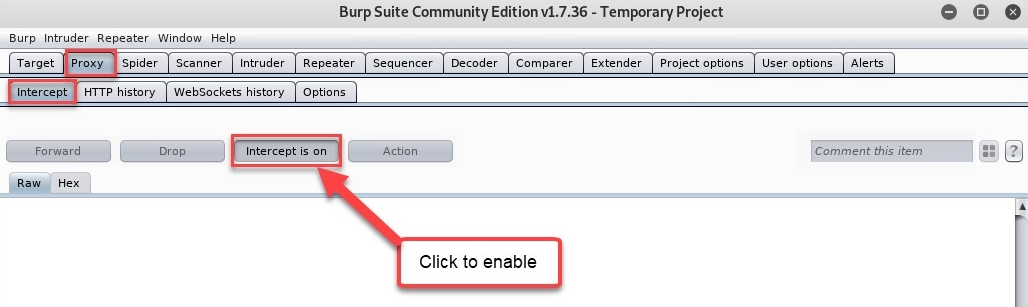
Ensure your configurations are set properly or the exercise won't work as it's intended to.
- Next, enter the IP address of the OWASP BWA virtual machine within the address bar in Firefox on your Kali Linux machine. The default web page should load perfectly. On Burp Suite, click on Target | Site Map to see the HTTP requests and responses:

- On the web browser, enter the URL (or IP address) of the OWASP BWA virtual machine. The HTTP requests and responses will appear on the Target | Site Map tab on Burp Suite.
Now that we've outlined how to intercept web traffic using Burp Suite, let's go a step further to perform an offensive attack on our Metasploitable machine. In the next section, we will use Burp Suite to perform a brute force attack.
