The Intruder component/module within Burp Suite allows a penetration tester to perform online password attacks using the brute force method. Let's attempt to obtain the password to log in to the http://<target ip addr>/mutillidae URL:
- Using the Firefox web browser click on Mutillidae II. On Burp Suite, you should see the mutillidae folder appearing under the left pane of the Site map tab.
- Next, right-click on the mutillidae folder, and select Add to scope as shown in the following screenshot:

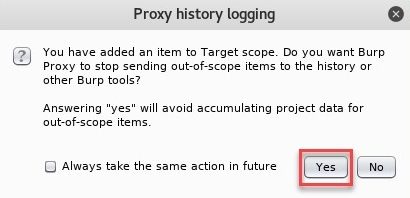
- The following Proxy history logging window will appear; simply click on Yes:
- To verify our scope has been added successfully, go to the Target | Scope tab:

- Now your scope has been added, head back to your web browser. At the top of the Mutillidae web page, you'll see a link that allows a user to perform login attempts. Use admin for the username and password for the password. The login attempt should fail; however, we need Burp Suite to capture specific details about the login field on the web page.
Let's head back to Burp Suite to continue our exercise.
- On Burp Suite, click on the Proxy | HTTP history tab and select the HTTP POST message, which has the login attempt from our browser (your # message may be different from what is shown in the following snippet). Once selected, right-click and choose Send to Intruder:

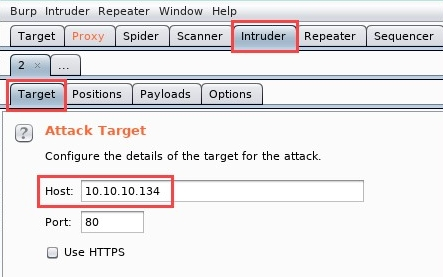
- Next, click on the Intruder | Target tab to see the target IP address that has been set:
Within the Intruder tab, there are a few sub-tabs, including the following:
-
- Target: Allows you to set a specific target and port number.
- Positions: Allows you to select where a payload will be inserted into the HTTP request.
- Payloads: Provides the ability to configure the type of payload.
- Options: Additional options can be set on this tab.
- Select the Positions tab and click on the Clear button to clear all selections. By default, Burp Suite has selected certain areas of the HTTP request message to insert its payload. However, for our exercise, the payload is to be inserted in the password field.
- Highlight the word password and click on Add. This will allow Burp Suite to insert its payload on the selected field:
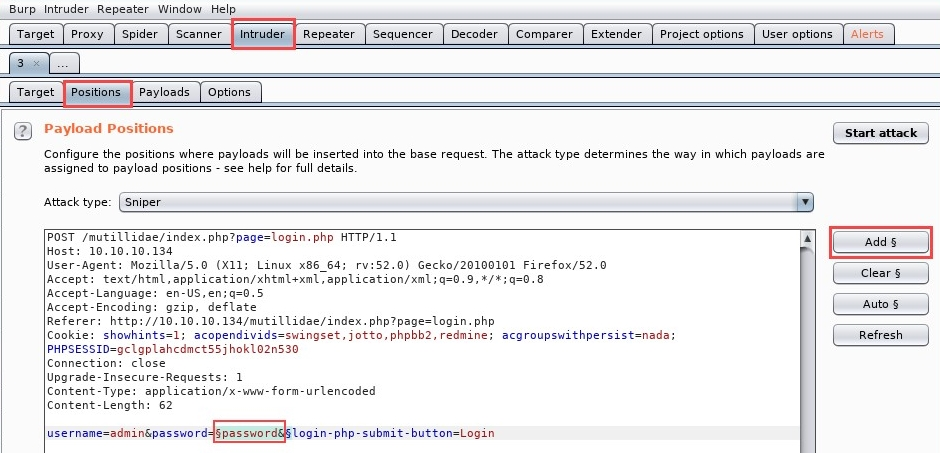
The red text is the data sent from the browser to the web server. As you can see, the word password is the value we used during our login attempt.
- Click on the Payloads tab. Enter admin in the text field and click Add; this will be our custom payload:
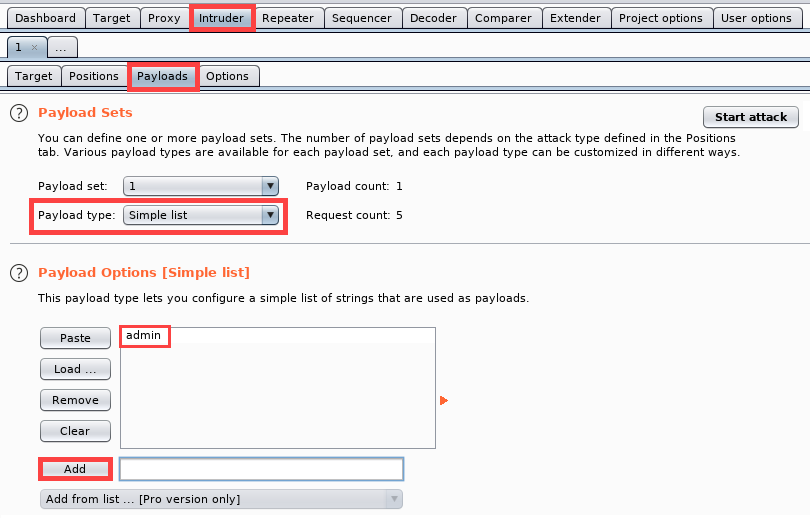
Ensure everything else is left as default in the remaining portions of the Payloads and Options tabs.
- When you're ready to launch the payload, click on Start attack:
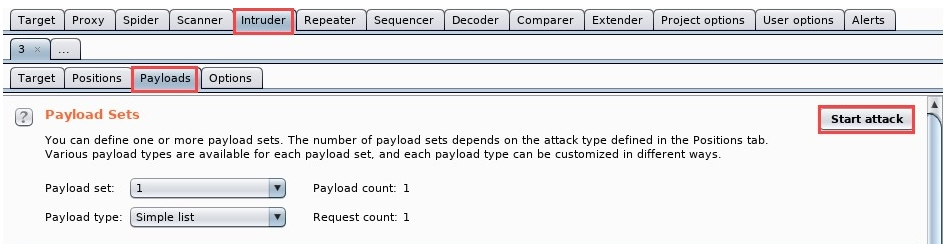
When the attack has been completed, Intruder will open a new window to provide a summary. On the Results tab, notice we have an HTTP request message with a 302 status code; this means an HTTP redirect took place. In other words, Intruder was able to successfully log in to Mutillidae. The details can be seen in the following screenshot with username and password:
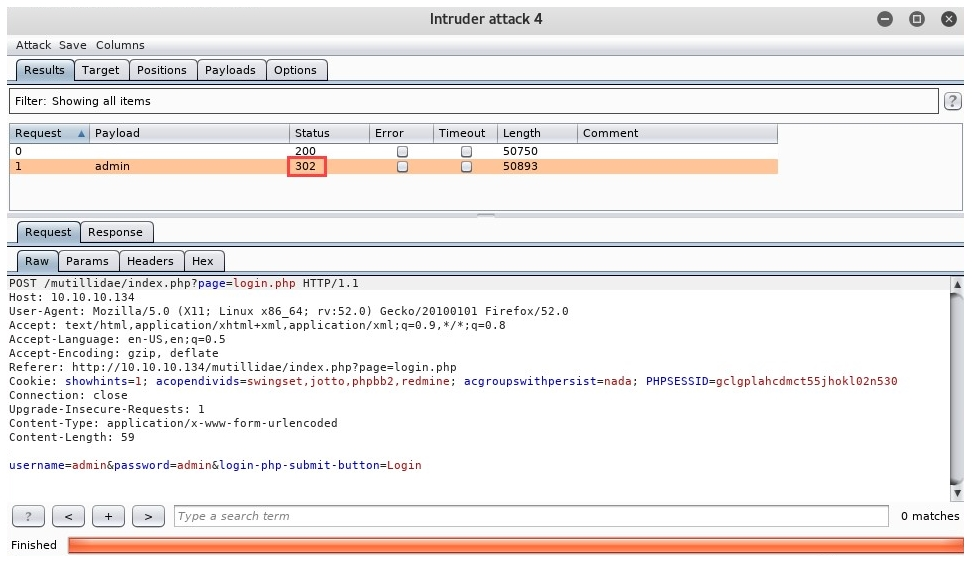
Selecting the HTTP request message with the 302 status code, you see the username and password that were sent from the web browser on the Request tab.
- To view the response from the web server, click on the Response | Render tab. Here you will be able to see how the web application responded to the payload:
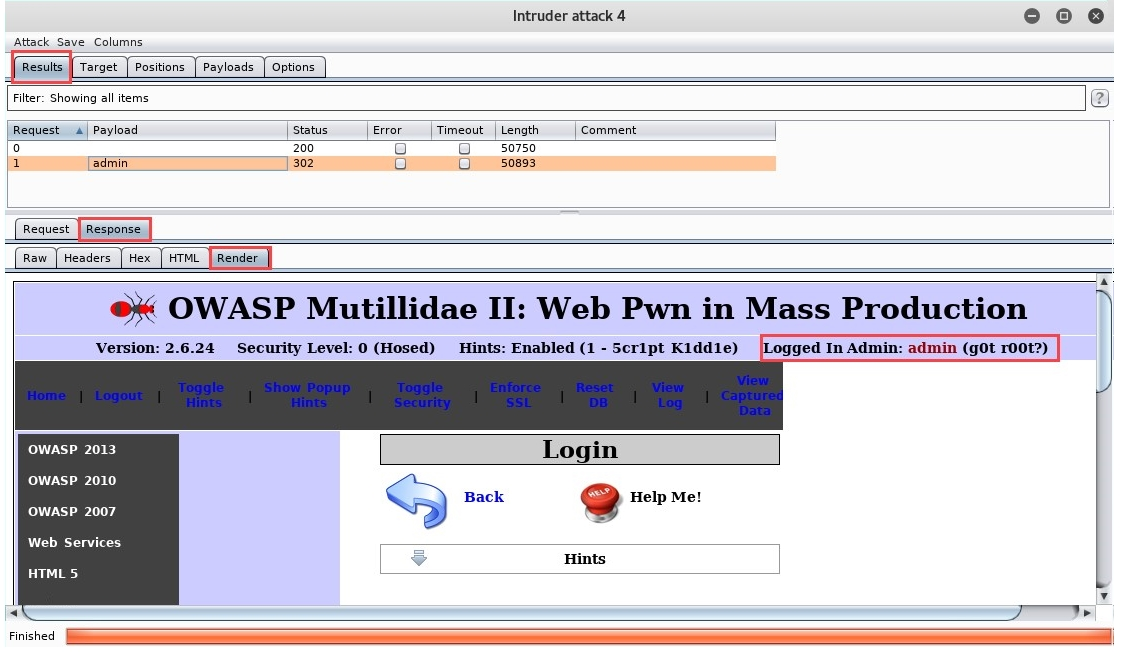
Looking closely, you'll see the admin user account was successfully logged in. Please note that the user account shown in the preceding screenshot is the default administration account for the intentionally vulnerable Metasploitable virtual machine. Furthermore, do not try any sort of attack on devices or networks where you have not acquired legal permission to do so. This exercise was conducted in a lab environment.
As you saw, Burp Suite is a very powerful application for web penetration testing and vulnerability assessments. This tool should definitely be part of your go-to list of tools whenever you're tasked with performing security auditing on a web server and website.
