Servers that are vulnerable to LFI security flaws allow an attacker to display the content of files through the URL within a web browser. In an LFI attack, the penetration tester can read the content of any file from within its directory using either ../ or /.
To get started, let's head back over to the Damn Vulnerable Web Application (DVWA) web interface within OWASP BWA:
- On the DVWA web interface, on the left-hand side menu, click on File Inclusion:

- By repeating ../ a few times and inserting the directory of the passwd file, we are able to view the content of the passwd file on the target web server:
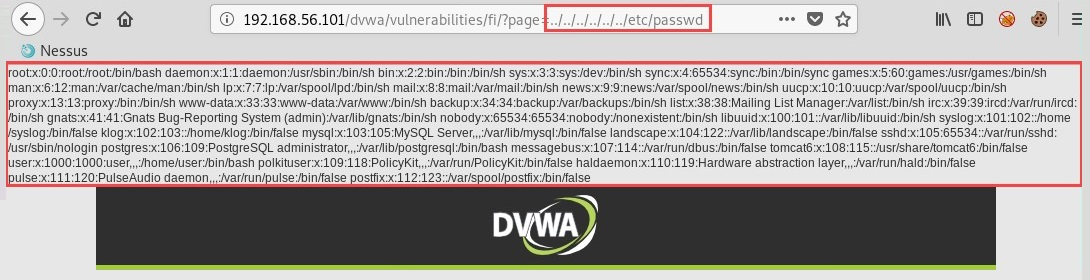
This type of attack tests a system for directory transversal vulnerabilities. Directory transversal allows an attacker to access restricted locations and files, as well as execute commands on a target web server. This attacker can manipulate the variables by simply using the dot-dot-slash (../) syntax within the URL.
Thus far, we have completed a few exercises to exploit the various weaknesses of a target system. In the next section, we'll take a look at preventing and mitigating security vulnerabilities.
