As a future penetration tester or ethical hacker, you may be tasked with conducting extensive wireless security testing for your company or a client organization. Creating a rogue AP with an interesting SSID (wireless network name), such as VIP_WiFi or Company-name_VIP, will lure employees to establish a connection.
In creating a rogue AP, the objective is to capture user credentials and sensitive information and to detect any vulnerable wireless clients in an organization. The following are some tips to consider when deploying your rogue AP:
- Choose a suitable location to ensure there is maximum coverage for the potential victims.
- Deauthenticate clients from the real AP, causing them to create an association with the rogue AP.
- Create a captive portal to capture user credentials.
To get started, we are going to use Airgeddon. This tool contains a lot of features and functions that will assist us, from gathering information about a target wireless network and its clients to launching various types of attacks and luring users to associate with our rogue AP.
To get started with creating a fake access point, please follow these steps:
- Download Airgeddon from its GitHub repository and give the airgeddon.sh script executable permissions on your user account. Use the following commands:
git clone https://github.com/v1s1t0r1sh3r3/airgeddon.git
cd airgeddon
chmod +x airgeddon.sh
- On your Terminal window, use the ./airgeddon.sh command to start the Airgeddon interface. Once the script has been initiated, Airgeddon will begin checking for the essential hardware and software requirements on your Kali Linux machine.
- Hit Enter a few times until you've reached the interface selection prompt; be sure to select your wireless adapter, as shown in the following screenshot:
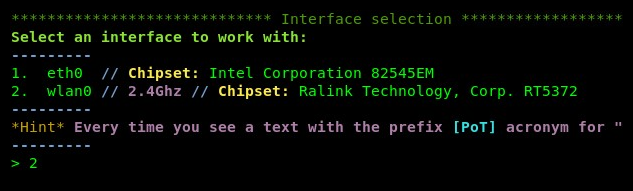
Select option 2, which has the wlan0 interface, and hit Enter.
- You'll now be presented with the main dashboard of Airgeddon. Here, you can choose to switch between monitor or managed mode on your wireless adapter. You'll be able to launch various types of attacks, such as Denial-of-Service (DoS) attacks, attempt to crack wireless passwords, capture and decrypt wireless handshakes, perform an evil twin attack, or create a rogue AP:
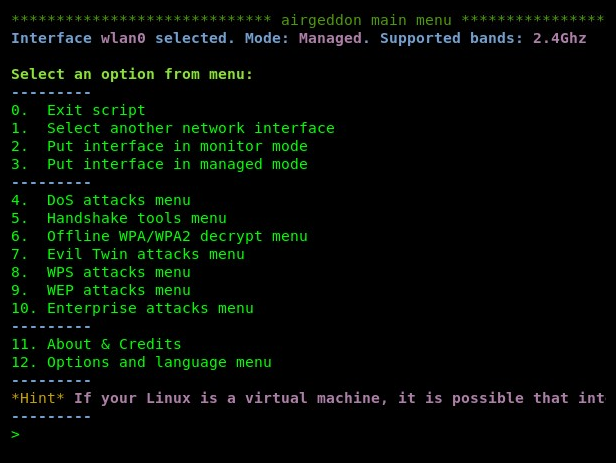
For our attack, we are going to create a honeypot to lure victims into connecting to our fake AP to intercept, redirect, and capture sensitive information.
- Next, set your wireless adapter to monitor mode. You can do this within the Airgeddon menu using the Put interface in monitor mode option. Once completed, you should see the status of your wireless adapter now changed to Monitor mode, as shown in the following screenshot:

- Select the Evil Twin attacks menu option and hit Enter. You'll be presented with the following options:
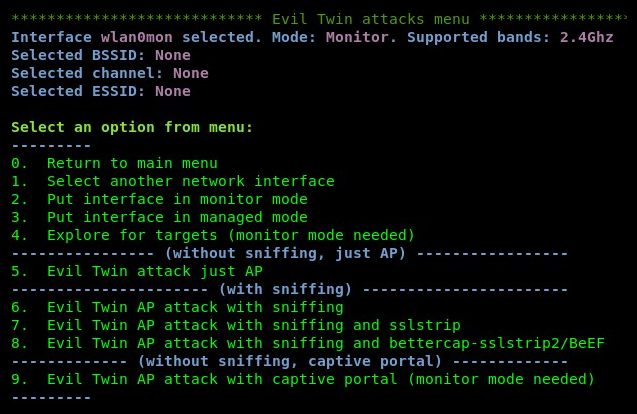
Not only does Airgeddon allow us to easily set up a rogue AP or evil twin, but it also provides us with additional features, such as sniffing the victim's traffic, performing SSL stripping of any SSL/TLS connections, performing browser exploitation, and even creating a captive portal for gathering user credentials.
- Let's first look for a target. Choose option 4 and hit Enter. A pop-up Terminal window will open, displaying all nearby APs. When you're ready to choose a target, choose the scanning window:
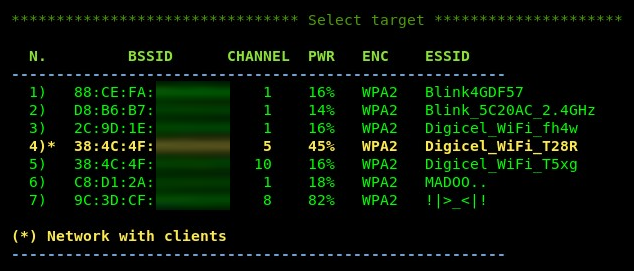
- Choose your target AP and hit Enter to continue. At this point, we have set our wireless adapter to Monitor mode and chosen our target:
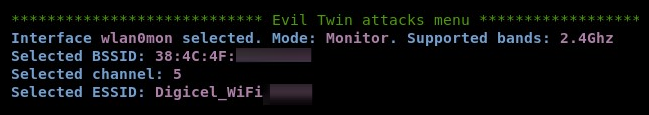
- Let's perform an evil twin attack with sniffing. Choose option 6 and hit Enter. The following menu will become available:
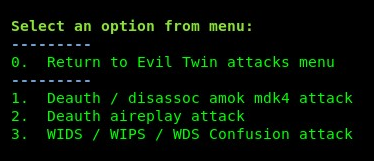
- Select option 2 to perform a deauthentication attack to the target wireless network; this will force the clients of the real network to disconnect (deauthenticate) and they will attempt to connect to our rogue AP/evil twin. Airgeddon will ask you to choose a physical interface that is connected to the internet/physical network. The purpose is to provide the illusion of regular network connectivity to the victims. When they are connected and accessing the local resources, the victims will think it's the legitimate network:
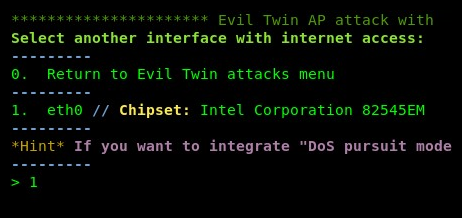
- Choose the appropriate interface and hit Enter to continue; hit Enter once more to verify the selected interface.
- When you're ready, launch the attack. Airgeddon will open a few smaller Terminal windows displaying the status of each attack it's performing, as shown in the following screenshot:

Once a client is connected, the appropriate Terminal window will provide you with an update. With just a few steps, you now have your own rogue AP/evil twin.
In the next section, we will discuss and demonstrate password spraying on a target system.
