During an MITM attack, the attacker is able to intercept all the traffic between the victim and the intended destination for their communication. Encrypted data will not be readable by an attacker; however, the attacker will still be able to view the following details, despite the encryption:
- Source IP address
- Destination IP address
- Source port
- Destination port
- Layer 3 protocol
On the attacker's machine, they will only be able to view the traffic that has been sent in plain text. The following screenshot shows a Wireshark capture between a client and a Linux server on a network:
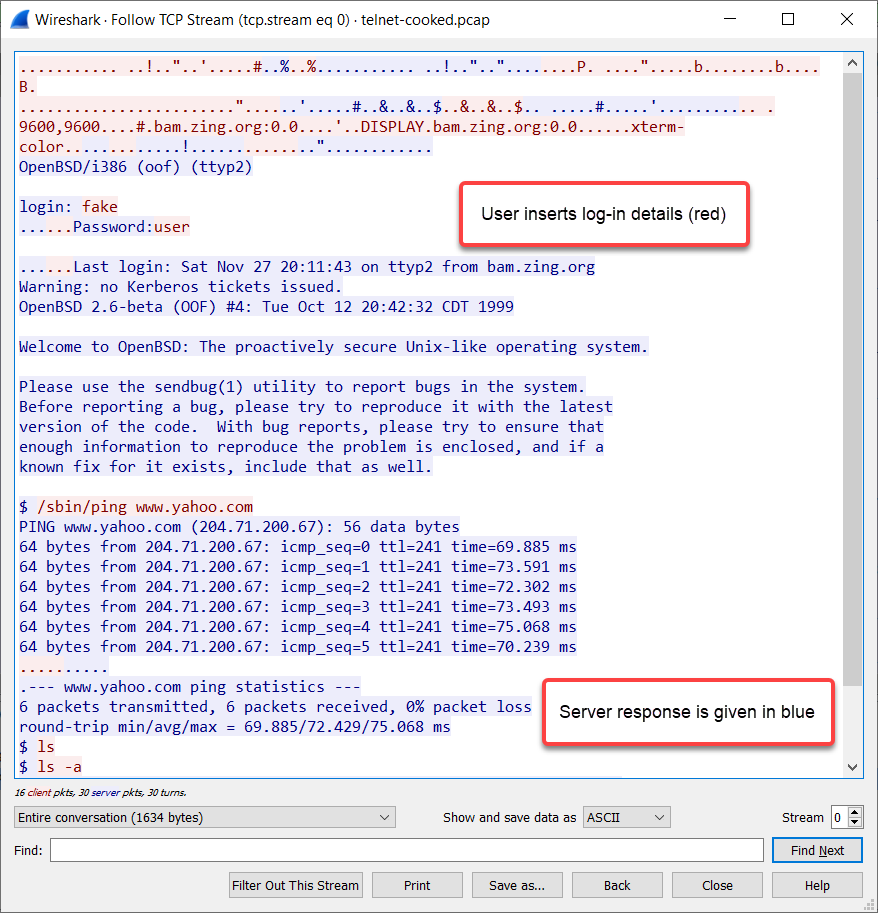
The server is using Telnet as its method of remote access. The user's input is given in red, while the server responses are given in blue. Here, we can see that Wireshark has reassembled all the Telnet packets for the entire conversation and is presenting it in a beautiful dialog format. In other words, we can see everything that happened during the Telnet session between both devices. In this capture, the username and password were recorded.
Preventing MITM attacks is critical on corporate networks as, every second, sensitive information is being sent across the organization in many formats.
In the following section, we will learn about how to configure a Cisco IOS switch with DAI.
