In stored XSS, the penetration tester injects malicious code that will be stored in the target database.
In this exercise, we will walk through the process of discovering a stored XSS vulnerability on a target server.
To complete this task, use the following instructions:
- Navigate to the bWAPP application and log in.
- Choose Cross-Site Scripting - Stored (Blog) and click on Hack to enable this vulnerability page:
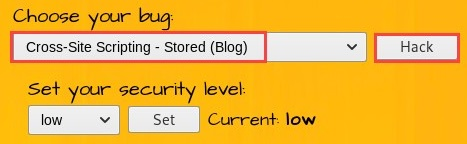
- You can enter any message within the text field and click Submit. The text entered will now be stored within the database, as in an online message board, forum, or website with a comments section:

Additionally, we can see the table, the field, and the columns.
- We can enter the following script within the text field and click Submit:
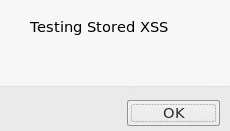
<script>alert("Testing Stored XSS")</script>
- After submitting the script, you'll receive the following pop-up window verifying that it ran successfully:
Looking at the table, there is a second row without any actual entry:
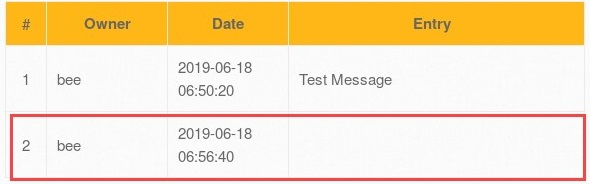
This new entry reflects that our script has been inserted and stored in the database. If anyone opens this web page, the script will automatically execute.
In the following section, we will demonstrate how to exploit XSS vulnerabilities using the Browser Exploitation Framework (BeEF).
