In checking for a stateful firewall, we can send a probe to the target with the ACK flag enabled. If no response is provided from the target, this would indicate that a firewall is present:
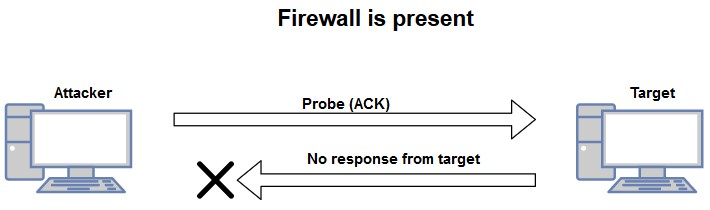
However, if a packet is returned with the RST flag set, this would indicate that there is no firewall on the target system:
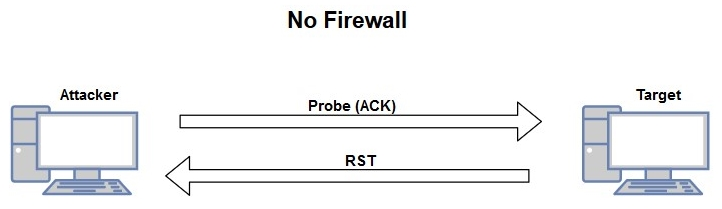
We can use the –sA operator on Nmap to perform an ACK scan on a target. Let's perform a scan on our Metasploitable VM to determine whether port 80 is open, and whether the system has a firewall present:
- Use the nmap -sA -p 80 <target> command:

- We were able to identify port 80 as opened and unfiltered (no firewall) on the target. Additionally, by observing the packets, we saw that an RST packet was returned to our Kali Linux (attacker) machine:

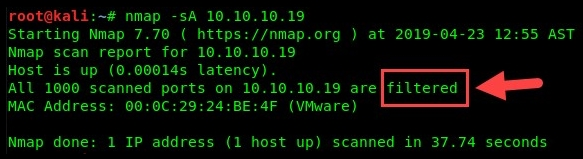
Whenever you run a scan on a target and the results indicate filtered, this means there is a firewall present and that it's actively monitoring the port, as shown in the following screenshot:
Additionally, the following operators can be used to determine whether a firewall is present on a system:
| Operator | Description |
| -sX | Performs an XMAS scan. The URG, FIN, and PSH flags are all set. |
| -sF | Performs a FIN scan. Only the FIN flag is set. |
| -sN | Performs a Null scan. No flags are set. |
Nmap will interpret the responses and determine whether the ports on a target are filtered or unfiltered.
Having completed this section, you are now able to use Nmap to profile a target. In the next section, we will learn about the Nmap Scripting Engine (NSE).
